**Methods of Encryption** I was unable to use the editor for this post, instead I had to use Markdown, so I apologize if there are formatting issues. If you are new to my Cryptology Series or are having trouble with any of the terminology, I encourage you to go to my blog and check out parts 1,2 and 3. Now let's get started! https://i.imgsafe.org/b6fbe822a4.png **Substitution Ciphers** Replaces bits, characters or blocks with different bits, characters or blocks. Caesar cipher is a substitution cipher Eample CAT=FDW **Transposition/ Permutation Cipher** Values are scrambled or put into a different order Uses P boxes Example. CAT=TCA Key=312 Substitution and transposition ciphers are relatively weak because of frequency analysis. In every language certain letters are used more often than others and in certain patterns, computers can perform frequency analysis to reconstruct text. 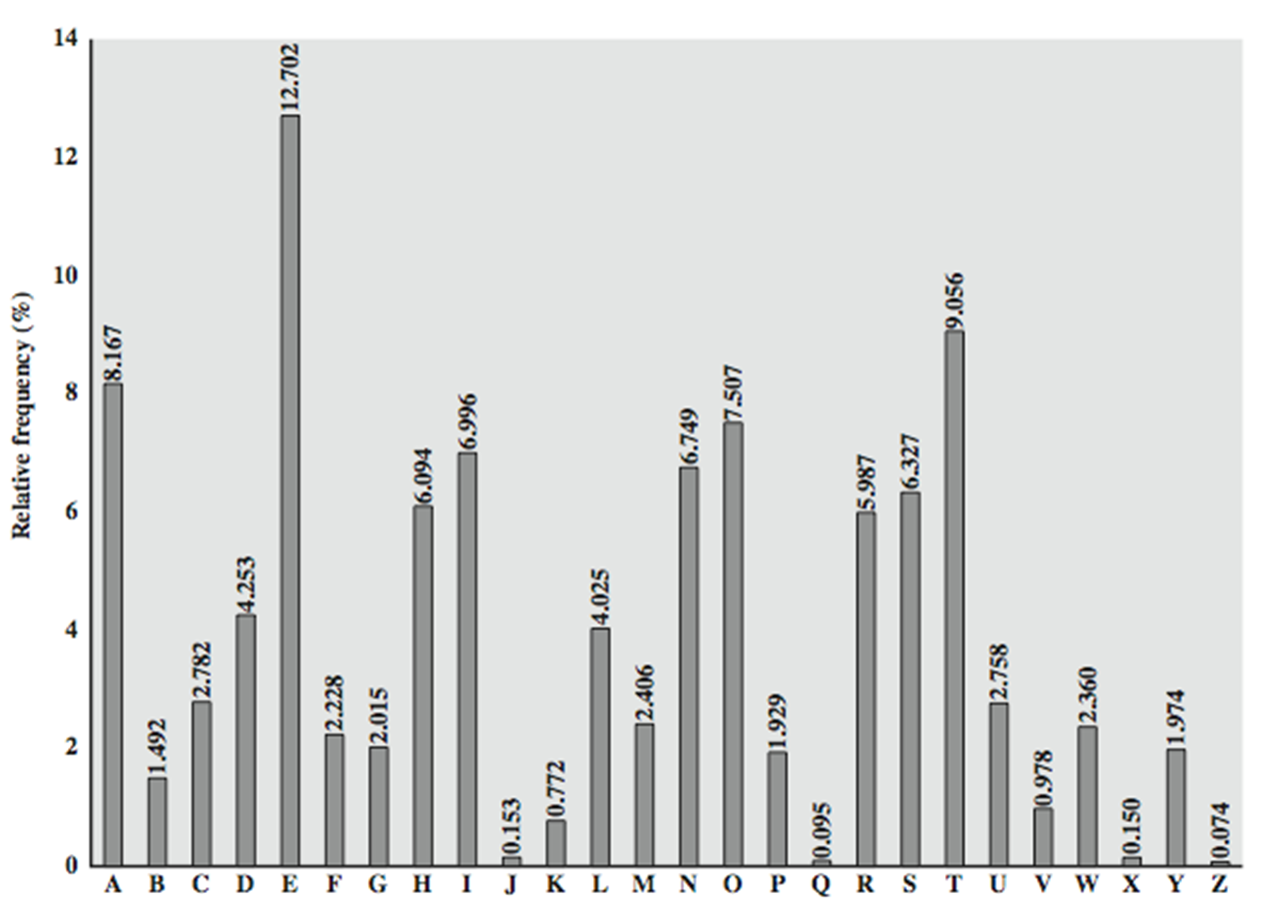 **Multi product cipher** A stronger cipher is multi product which combines both substitution and transposition. Example. Plain Text= CAT Substitution=FDW Transposition=312 Multi product = WFD **Methods of Encryption** **Symmetric Cryptography** Uses symmetric keys known as secret keys, sender and receiver use two instances of the same key Benefit: much faster and less computationally intensive Weakness: Secure key distribution **Asymmetric Cryptography** Two different asymmetric keys that are mathematically related One public and one private key Benefit: better key distribution Weakness: slower 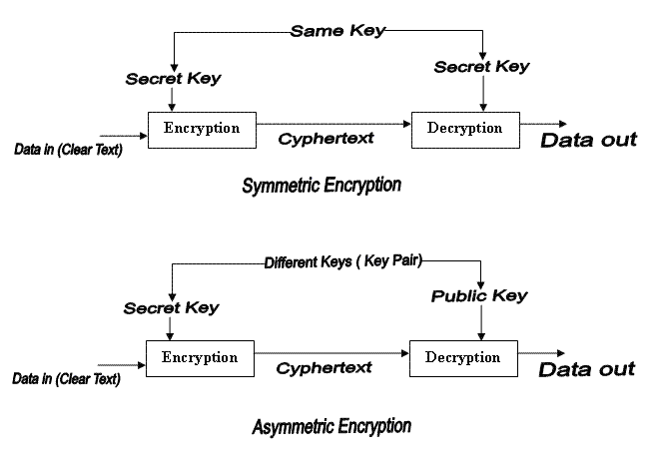 **Hybrid Encryption** Public key cryptography uses two keys, a public key generated by an asymmetric algorithm and a private key generated by a symmetric algorithm. Symmetric is used for bulk encryption Asymmetric is used to encrypt the private key for secure key distribution **Block Ciphers** Message is divided into blocks of bits, then put through the mathematical functions one block at a time. https://i.imgsafe.org/be670eba9d.png **Stream Cipher** Stream ciphers process messages a bit or byte at a time when en/decrypting Stream ciphers use a key stream generators, which produce a stream of bits that is XORed with the plaintext bits to produce ciphertext. 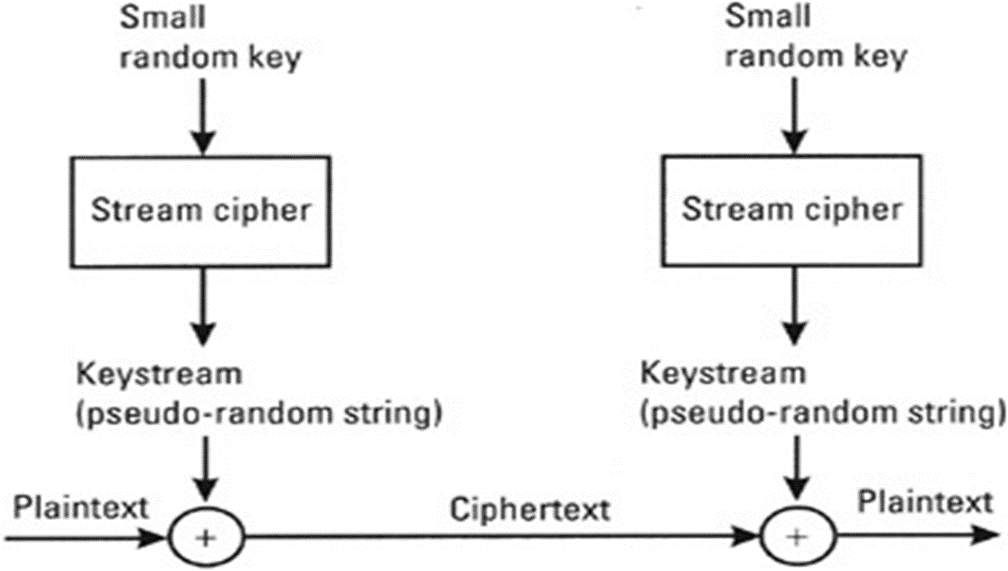 **Confusion vs Diffusion** Confusion is commonly carried out through substitution. Makes the relationship between the key and the resulting cipher text, making it complex so key cannot be identified Diffusion is carried out by using transposition. dissipates statistical structure of plaintext over bulk of cipher text **Avalanche Effect** **Avalanche Effect**- if the input to an algorithm is slightly modified then the output of the algorithm is changed significantly **Cryptographic Transformation** **Initialization Vectors**- random values in algorithm used to ensure patterns are not created in the encryption process. **Compression**- reduce redundancy before PT is encrypted. **Expansion**- expanding the PT by duplicating values. Commonly used to increase PT size to map key sizes. **Padding**- adding material to PT before it is encrypted. **Key mixing**-using a portion (subkey) of a key to limit the exposure of the key. Key schedules are used to generate sub keys **There will be a part 5 and 6 to the Cryptology Series** **I will also be holding another Cryptography challenge where you can win STEEM!** **I have a few other exciting projects in the works that I hope you will like, stay tuned!** Follow my blog @digicrypt if you are interested in cryptocurrency, cryptology or blockchain. **DASH**: XgQ9NBonMoCPKhF37agY4W8zk7gwQFnwGV **Ether**: XE04RO3I0QA5UKB31OZK4O3CK3TOT03R4TM https://i.imgsafe.org/be8afb8c2a.png https://logomakr.com/
| author | digicrypt |
|---|---|
| permlink | cryptology-series-part-4-methods-of-encryption |
| category | cryptocurrency |
| json_metadata | {"tags":["cryptocurrency","bitcoin","life","cryptology","history"],"users":["digicrypt"],"image":["https://i.imgsafe.org/b6fbe822a4.png","https://steemitimages.com/DQmbiemo3DYRxkb8VCCWm4bG4Qh4DkDqGy5bCtvGa17vZsV/image.png","https://steemitimages.com/DQmYDjbdifFQ7avRAuAYSe66XWWL3Yy7UJWPcYsAv29sZsc/image.png","https://i.imgsafe.org/be670eba9d.png","https://steemitimages.com/DQmcK7rQFk62gWWWaEcfDtwZ22PSkaH5SnRZcByuTFnLpDP/image.png","https://i.imgsafe.org/be8afb8c2a.png"],"links":["https://logomakr.com/"],"app":"steemit/0.1","format":"markdown"} |
| created | 2017-03-29 17:17:18 |
| last_update | 2017-03-29 17:17:18 |
| depth | 0 |
| children | 5 |
| last_payout | 2017-04-05 17:17:18 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.038 HBD |
| curator_payout_value | 0.007 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.002 HBD |
| body_length | 3,935 |
| author_reputation | 9,344,424,618,224 |
| root_title | "Cryptology Series Part 4: Methods of Encryption" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 2,889,456 |
| net_rshares | 1,603,711,305,564 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| hr1 | 0 | 730,737,540,134 | 100% | ||
| pairmike | 0 | 3,780,227,651 | 1% | ||
| proctologic | 0 | 3,804,647,284 | 1% | ||
| konelectric | 0 | 416,056,948 | 1% | ||
| forrestwillie | 0 | 498,754,584 | 1% | ||
| slickwilly | 0 | 103,597,654,512 | 100% | ||
| andrei | 0 | 235,504,290 | 1% | ||
| fyrstikken | 0 | 53,069,510,732 | 1% | ||
| matt-a | 0 | 144,641,685,912 | 100% | ||
| spiz0r | 0 | 54,066,416,196 | 100% | ||
| jamesjarman | 0 | 1,708,929,744 | 1% | ||
| juvyjabian | 0 | 624,923,008 | 1% | ||
| karenmckersie | 0 | 2,328,812,580 | 1% | ||
| raymonjohnstone | 0 | 10,488,510,835 | 100% | ||
| youngkim | 0 | 471,533,311 | 1% | ||
| dirty.hera | 0 | 56,020,131 | 1% | ||
| gomeravibz | 0 | 1,801,941,767 | 1% | ||
| timelapse | 0 | 463,521,659 | 1% | ||
| t3ran13 | 0 | 5,746,995,215 | 100% | ||
| riosparada | 0 | 48,228,596,308 | 100% | ||
| steemitqa | 0 | 291,952,540 | 1% | ||
| darthnava | 0 | 436,577,954 | 1% | ||
| cryptos | 0 | 67,985,195,875 | 50% | ||
| mrosenquist | 0 | 81,661,635,208 | 100% | ||
| lasseehlers | 0 | 1,219,823,291 | 1% | ||
| shadowspub | 0 | 605,793,020 | 1% | ||
| runridefly | 0 | 4,190,900,538 | 11% | ||
| barrydutton | 0 | 2,257,649,678 | 1% | ||
| jlufer | 0 | 9,432,676,604 | 100% | ||
| contentjunkie | 0 | 49,334,943,879 | 100% | ||
| steemitguide | 0 | 624,202,361 | 1% | ||
| azz | 0 | 81,437,074 | 100% | ||
| richardcrill | 0 | 1,260,648,522 | 1% | ||
| jag | 0 | 78,567,883 | 100% | ||
| reaction | 0 | 1,538,553,418 | 100% | ||
| jacobts | 0 | 354,616,815 | 1% | ||
| mindhunter | 0 | 1,596,962,089 | 1% | ||
| patelincho | 0 | 251,410,334 | 1% | ||
| movietrailers | 0 | 2,430,804,687 | 100% | ||
| statsbot | 0 | 74,136,732 | 100% | ||
| newsbot | 0 | 74,120,850 | 100% | ||
| crashoverride | 0 | 50,124,308 | 100% | ||
| cartman | 0 | 239,536,406 | 100% | ||
| surpassinggoogle | 0 | 541,968,585 | 1% | ||
| dickbutt | 0 | 112,857,639 | 100% | ||
| peeweeherman | 0 | 118,300,191 | 100% | ||
| cowboycurtis | 0 | 102,559,507 | 100% | ||
| jambii | 0 | 102,541,215 | 100% | ||
| coolcat | 0 | 179,023,682 | 100% | ||
| opall | 0 | 178,371,409 | 100% | ||
| elviss | 0 | 152,787,961 | 100% | ||
| chair | 0 | 178,797,159 | 100% | ||
| conky | 0 | 212,254,308 | 100% | ||
| dademurphy | 0 | 177,381,750 | 100% | ||
| chart | 0 | 176,571,488 | 100% | ||
| mrssteve | 0 | 177,062,777 | 100% | ||
| towelie | 0 | 612,339,712 | 100% | ||
| philipjfry | 0 | 393,785,234 | 100% | ||
| mrhanky | 0 | 175,585,252 | 100% | ||
| popcornmachine | 0 | 175,477,639 | 100% | ||
| wilburtsmythe | 0 | 175,083,695 | 100% | ||
| bitrx | 0 | 174,722,784 | 100% | ||
| bluetrade | 0 | 174,024,462 | 100% | ||
| shape | 0 | 173,589,893 | 100% | ||
| lydon.sipe | 0 | 40,588,800,875 | 100% | ||
| highfive | 0 | 171,533,859 | 100% | ||
| jebus | 0 | 171,450,324 | 100% | ||
| clarence | 0 | 171,440,496 | 100% | ||
| steemet | 0 | 170,583,709 | 100% | ||
| qantheman | 0 | 169,427,301 | 100% | ||
| charity | 0 | 168,363,691 | 100% | ||
| annul | 0 | 168,251,211 | 100% | ||
| suntzu | 0 | 167,071,981 | 100% | ||
| mchammer | 0 | 167,039,031 | 100% | ||
| vanilla | 0 | 166,281,445 | 100% | ||
| guerilla | 0 | 166,073,800 | 100% | ||
| icet | 0 | 165,927,731 | 100% | ||
| nedd | 0 | 165,208,397 | 100% | ||
| kickass | 0 | 164,565,366 | 100% | ||
| oreo | 0 | 164,481,990 | 100% | ||
| curei | 0 | 163,205,407 | 100% | ||
| currie | 0 | 162,253,462 | 100% | ||
| giantbear | 0 | 1,412,565,478 | 1% | ||
| austinpowers | 0 | 160,376,631 | 100% | ||
| shapeshifter | 0 | 158,812,591 | 100% | ||
| stun | 0 | 158,378,363 | 100% | ||
| icecube | 0 | 157,785,962 | 100% | ||
| view | 0 | 157,739,542 | 100% | ||
| kitt | 0 | 156,417,008 | 100% | ||
| katt | 0 | 156,199,419 | 100% | ||
| itchy | 0 | 156,135,553 | 100% | ||
| scratchy | 0 | 156,128,043 | 100% | ||
| krusty | 0 | 155,875,598 | 100% | ||
| scene | 0 | 155,562,953 | 100% | ||
| fyrst-witness | 0 | 23,651,497,807 | 100% | ||
| quimby | 0 | 154,161,478 | 100% | ||
| wiggum | 0 | 156,191,366 | 100% | ||
| sideshowbob | 0 | 153,025,956 | 100% | ||
| daisyd | 0 | 401,482,779 | 1% | ||
| drnick | 0 | 718,959,161 | 100% | ||
| whatageek | 0 | 961,057,642 | 1% | ||
| fentan99 | 0 | 2,165,263,131 | 100% | ||
| gutzofter | 0 | 94,433,898,048 | 100% | ||
| mls | 0 | 892,239,789 | 100% | ||
| butan | 0 | 107,247,513 | 1% | ||
| seablue | 0 | 2,104,430,809 | 1% | ||
| valiozzi | 0 | 0 | 0% | ||
| meysam | 0 | 672,488,516 | 1% | ||
| ladder | 0 | 681,084,195 | 100% | ||
| darth-azrael | 0 | 5,811,074,250 | 80% | ||
| driptorchpress | 0 | 91,407,039 | 1% | ||
| riskdebonair | 0 | 1,117,600,572 | 1% | ||
| darth-cryptic | 0 | 1,277,906,792 | 100% | ||
| steemstock | 0 | 673,250,867 | 100% | ||
| stonedfood | 0 | 8,947,687,019 | 100% | ||
| cwatch | 0 | 152,607,149 | 1% | ||
| willsplace | 0 | 64,885,442 | 1% | ||
| ambyr00 | 0 | 3,026,830,755 | 1% | ||
| writemore | 0 | 556,196,586 | 100% | ||
| digicrypt | 0 | 8,660,738,571 | 100% | ||
| mycryptomark | 0 | 69,636,848 | 1% | ||
| deepapoudel | 0 | 2,129,379,058 | 100% | ||
| dracosalieri | 0 | 0 | 100% | ||
| chasmic-cosm | 0 | 0 | 100% | ||
| timothy-archer | 0 | 0 | 100% |
Upvoted and resteemed!!!!!!
| author | riosparada |
|---|---|
| permlink | re-digicrypt-cryptology-series-part-4-methods-of-encryption-20170330t011858294z |
| category | cryptocurrency |
| json_metadata | {"tags":["cryptocurrency"],"app":"steemit/0.1"} |
| created | 2017-03-30 01:18:57 |
| last_update | 2017-03-30 01:18:57 |
| depth | 1 |
| children | 1 |
| last_payout | 2017-04-06 01:18:57 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 27 |
| author_reputation | 90,448,613,328,349 |
| root_title | "Cryptology Series Part 4: Methods of Encryption" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 2,893,830 |
| net_rshares | 56,903,253,984 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| riosparada | 0 | 48,228,596,308 | 100% | ||
| digicrypt | 0 | 8,674,657,676 | 100% |
Thank you and thanks for the resteem! Much appreciated!
| author | digicrypt |
|---|---|
| permlink | re-riosparada-re-digicrypt-cryptology-series-part-4-methods-of-encryption-20170330t012923103z |
| category | cryptocurrency |
| json_metadata | {"tags":["cryptocurrency"],"app":"steemit/0.1"} |
| created | 2017-03-30 01:29:21 |
| last_update | 2017-03-30 01:29:21 |
| depth | 2 |
| children | 0 |
| last_payout | 2017-04-06 01:29:21 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 55 |
| author_reputation | 9,344,424,618,224 |
| root_title | "Cryptology Series Part 4: Methods of Encryption" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 2,893,913 |
| net_rshares | 0 |
<p>This post has been ranked within the top 80 most undervalued posts in the second half of Mar 29. We estimate that this post is undervalued by $2.62 as compared to a scenario in which every voter had an equal say.</p> <p>See the full rankings and details in <a href="https://steemit.com/curation/@screenname/the-daily-tribune-most-undervalued-posts-of-mar-29---part-ii">The Daily Tribune: Mar 29 - Part II</a>. You can also read about some of our methodology, data analysis and technical details in <a href="https://steemit.com/curation/@screenname/introducing-the-daily-tribune-most-undervalued-posts-of-nov-04---part-i">our initial post</a>.</p> <p>If you are the author and would prefer not to receive these comments, simply reply "Stop" to this comment.</p>
| author | screenname |
|---|---|
| permlink | re-cryptology-series-part-4-methods-of-encryption-20170330t013344 |
| category | cryptocurrency |
| json_metadata | "{"replyto": "@digicrypt/cryptology-series-part-4-methods-of-encryption"}" |
| created | 2017-03-30 01:33:45 |
| last_update | 2017-03-30 01:33:45 |
| depth | 1 |
| children | 0 |
| last_payout | 2017-04-06 01:33:45 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 765 |
| author_reputation | 46,276,338,038,330 |
| root_title | "Cryptology Series Part 4: Methods of Encryption" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 2,893,939 |
| net_rshares | 8,674,657,676 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| digicrypt | 0 | 8,674,657,676 | 100% |
Upvoted!!!!!
| author | steemstock |
|---|---|
| permlink | re-digicrypt-cryptology-series-part-4-methods-of-encryption-20170330t011720393z |
| category | cryptocurrency |
| json_metadata | {"tags":["cryptocurrency"],"app":"steemit/0.1"} |
| created | 2017-03-30 01:17:18 |
| last_update | 2017-03-30 01:17:39 |
| depth | 1 |
| children | 1 |
| last_payout | 2017-04-06 01:17:18 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 12 |
| author_reputation | 807,732,210,239 |
| root_title | "Cryptology Series Part 4: Methods of Encryption" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 2,893,815 |
| net_rshares | 8,674,657,676 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| digicrypt | 0 | 8,674,657,676 | 100% |
Thanks!
| author | digicrypt |
|---|---|
| permlink | re-steemstock-re-digicrypt-cryptology-series-part-4-methods-of-encryption-20170330t013438152z |
| category | cryptocurrency |
| json_metadata | {"tags":["cryptocurrency"],"app":"steemit/0.1"} |
| created | 2017-03-30 01:34:39 |
| last_update | 2017-03-30 01:34:39 |
| depth | 2 |
| children | 0 |
| last_payout | 2017-04-06 01:34:39 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 7 |
| author_reputation | 9,344,424,618,224 |
| root_title | "Cryptology Series Part 4: Methods of Encryption" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 2,893,944 |
| net_rshares | 0 |
 hiveblocks
hiveblocks