
If you haven't heard by now, world renown security expert, John McAfee had his Twitter account hacked around Christmas time when he was posting Coin of the Day updates that were causing quite a stir.
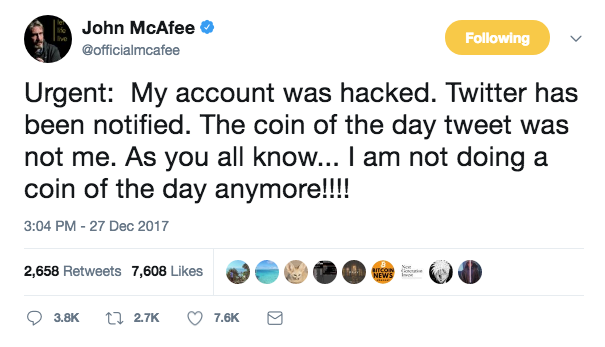
Surprisingly, at least to me, he admitted that it was via a hack he'd never heard of before. Here's what he said about the hack:
> “What happened is brand new to me. They managed to hack AT&T to move my phone number to another phone,” and then sent a bogus request for a Twitter password change. Since his telephone number was hijacked, there was little he could he do to stop hackers from successfully seizing his social media account, he said.
It's not McAfee's fault. He's a security guru, but he doesn't reside over Twitter's security team.
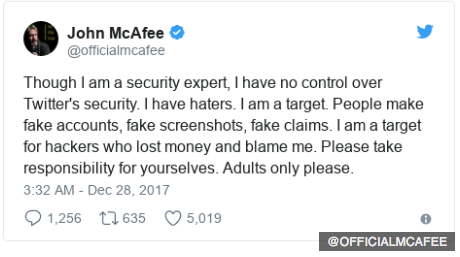
So how did it happen? In a nutshell, the hackers used a bit of social engineering and exploited human weakness at AT&T to convince the support person that he bought a new device with a new SIM card and had the new device activated with existing phone number. Once that was accomplished, the hackers simply requested a password reset on Twitter, to which the verification code was sent out to his phone number, which of course, now reaches the hacker's device instead of McAfee's.
If you don't believe it's possible to socially engineer a takeover of your phone, just watch this video to see how this woman hacks the interviewer's account in minutes and gets herself added as an authorized user on his account:
https://www.youtube.com/watch?v=lc7scxvKQOo
By now, if you're a crypto-currency trader, the hairs on the back of your neck should be bristling as you realize how many places you've set up 2FA login/authentication to protect your funds. McAfee's solution was to go around disabling 2FA on everything, but that is not always an option with all the exchanges you may be using, so just how do you go about protecting your accounts?
First, understand the minimum information a hacker needs to hack your phone and move your number to another SIM:
1. Your full name
1. Your phone number
Also helpful, but not necessary:
1. Your date of birth.
1. Your email.
1. Your spouse's name.
Obviously, the more information the hacker has, the better his chances to convincing a human he knows you as your spouse or he is, in fact, you. Any social media site, especially Facebook or Linked-In where your phone number, email, and birthdate has been posted makes your critical information public whether you checked all the privacy boxes or not.
Facebook has been attacked and leaked personal data time and time again. Yahoo, AOL, and even Experian have all been massively hacked with user's sensitive information widely circulated on the dark web. You must assume your information is out there if you ever supplied it to any the big social media sites or have a credit history to speak of.
If you have a significant amount of funds in crypto exchanges or on Coinbase or anywhere subjected to being heavily targeted by hackers, then you owe it to yourself to take action now to eliminate or reduce your risk exposure.
What follows is a simple game plan to foil most hacking attempts and at least severely raise the level of difficulty. In a nutshell, you will contact points only you ever use or know about, update the exchanges and is never shared on any of the major social media networks.
## Dedicated Email Address
First up, you will want to set up dedicated email address that you never use for emailing other humans, or at least not family, friends, and anywhere near social media outlets. This is your new "anonymous email address."
The idea is to have an email no one knows about and not subjected to being shared by your phone, your Facebook, Twitter, or other services designed to *increase* social participation. You will want to change all registrations on crypto currency exchanges to use this new email address.
Rules of Engagement:
1. Use this email for exchange account sign-ups and logins
2. Never share on Facebook, Twitter, or with Friends and Family. Never email anyone other than Tech support of the services you use it for.
3. Do not set up the email account on your mobile devices.
That last rule may surprise you, but goal is to separate 2FA (which is likely on your mobile device) entirely from access to your new and anonymous email address. And remember, mobile devices are designed to share your information. You're also unable to see into the innards of any apps you download and install and unable to control the basic security of your mobile devices to the extent you can control your desktop or notebook computer.
At any time that you think your email address is "burned" (that is, has been leaked or exposed unintentionally), replace it with a new email address and update everywhere the old anonymous email address was used. Protect your largest holdings first and less critical holdings last.
## Get a new mobile device with dedicated phone number
I cannot overstate that if you have previously filled out your mobile phone number anywhere in the social media realm, your number is essentially leaked. You do not want to use a leaked number for 2FA authentication on any site that has financial repercussions. A hacker targeting you, will gather your numbers that have been leaked and call service providers posing as you or your spouse and attempt to gain access to your accounts using that number.
Like your new anonymous email address, this new number is now your anonymous phone number and this should never see the light of day on a social media site. There's a couple of ways to obtain a new number and device to serve as your anonymous 2FA device:
1. Simply add a new line to your multi-line contract and pay the $30 ~ $40 a month to have it.
1. Download and use an app like [Burner App](https://www.burnerapp.com/).
1. Open an entirely new account with minimal service installed. Data/Texting is all you need for setting up and using 2FA.
Each has it's own pros and cons. For me, I already had a three-party line, so I opted to add another line and with T-Mobile, they had a great Revel Android phone for just $150 and cost me an extra $30/mo. I took an extra precaution of changing the primary phone on the account to another so that my well-known phone number cannot be used to primary vector to accessing the account.
## Put an unforgettable PIN on your Phone Account
Once you have your devices and new number, go ahead and ensure a PIN, preferably an 6 to 8 digit PIN is added on the account. One that is *not* based on you or your family's birthdates, SSN, or anything else that's a common go-to or default setting that the service providers often use.
## Lock down account changes to In Store Visits only
Finally, go to the nearest local store for your service provider and request that your account be locked down and serviceable only via in-store visits with presentation of photo ID. This will make things harder for you, but protects you from social engineering to a much greater degree. While I don't think this is absolutely foolproof from social engineering, I am most certainly sure it raises the barrier to entry high enough, that you'll likely get a call from the carrier or an automated email alert should repeated attempts to hack your account happen in a short period of time with this degree of protection in place and you will have time to take pre-emptive measure to lock things down or protect your funds by moving them offline for a while.
## Change your 2FA to your new Device and Number
Finally, change your 2FA on all Exchanges to your new device and number. Do *not* change social media or other non-financial related accounts to your new device and number.
The process is fairly simple if you have both your old and new devices in hand. You simply disable 2FA and authorize through your old device's 2FA, then add your new device when you opt to re-enable 2FA. Some sites, like Bittrex make it a bit of a pain by requiring a support ticket and waiting period, but by far and large, you'll be able to switch over most sites in a few minute's time.
## Are We Done, Yet?
By the time you have implemented all of the above, you'll have your new anonymous email set up on the exchanges along with your new anonymous phone number and 2FA all on your dedicated device.
If you're super paranoid, there are even more steps you can take, but the above raises the bar enough to keep all but a highly targeted attacks on your identity at bay. If you want to hear more on this topic, let me know in the comments and if the interest is there, I'll go even deeper with more advanced techniques for securing your identity from social engineered attacks.
Until next time: Happy and Safe Crypto Trading!
 hiveblocks
hiveblocks