 Hello Everyone, So far I've written primarily about Splinterlands but today I've decided I'd like to start a technical How-To series as it relates to IT security and auditing. This series and guide is intended for those of you just starting out in IT operations, IT compliance, and IT audit. We will be focusing on IT General Controls which generally cover Authentication, Authorization, and Change Management. To start this series off we are going to be talking about Windows because who isn't familiar with that. The risks associated with Windows and AD from a compliance and audit standpoint can be tied to the areas we discussed previously, the risk of inappropriately assigned access, inappropriately configured systems, and poor change management. In a mature environment these risks are formally mapped out against identified IT controls and tested internally by management, internal audit, and external audit. At the enterprise level, Windows is reliant on Active Directory (AD) which is a hierarchical structure, much like a database, that stores information about objects such as users on the network. The ability of AD to store this information allows Windows administrators to easily secure their environment by configuring and restricting the system and areas within the network to specific objects. **Privileged users and groups** Windows environments are shipped with a built-in privileged administrator account with the security ID (SID) 500. This ID is setup under the name 'Administrator' and effectively has all of the keys to the kingdom and should be priority 1 to secure. Best practice is to rename this ID and configure it to require smart card or other physical auth token for login. In addition, Windows has some default privileged groups, noted below, which provide critical access to configurations and user maintenance. These groups and the users within should be monitored regularly to ensure appropriateness. • Administrators • Domain Admins • Enterprise Admins • Group Policy Admins • Schema Admins • Account Operators • Server Operators 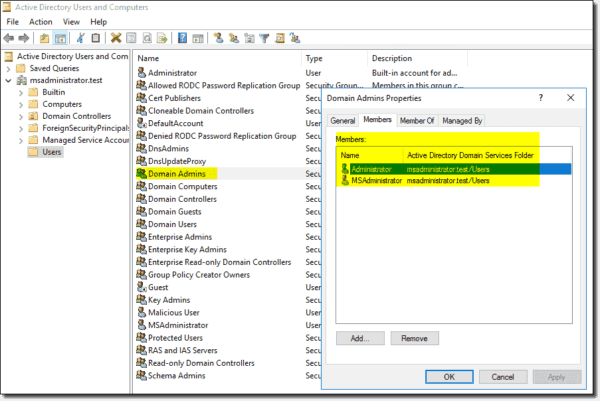 *image property of Microsoft Geek* In addition to the root domain controller, enterprise networks typically are used to connect all of the servers that run company applications, databases, and tools. Each of these individual servers also contain privileged users and should be monitored and configured in the same manner as the root level. That said, there are some differences. The Enterprise Admins and Schema Admins groups will only exist at the root domain. Each child domain has a set of the remaining groups and each child server more specifically would be managed by the Administrators group. In a mature environment, these groups and users would be reviewed on a periodic basis according to corporate policy. **Inappropriate configurations** One of the first areas of concern after ensuring access privileges are assigned properly is ensuring that the system itself is hardened, or difficult to get into. As simple as it sounds, authentication configurations such as basic password restrictions are the cornerstone to achieve this. Within Windows this is easily accomplished by setting a Default Domain Policy via a Group Policy Object. This policy should be set at minimum to corporate policy and the following attributes should be considered: • Minimum Password Length • Maximum Password Age (in Days) • Minimum Password Age (in Days) • Enforce Password History • Password Complexity • Lockout Threshold • Lockout Duration • Reset Lockout Counter (in Minutes) Although these settings 'can' be set globally, local servers can also block inheritance of the policy so these same settings should be enforced and checked locally within servers as well. 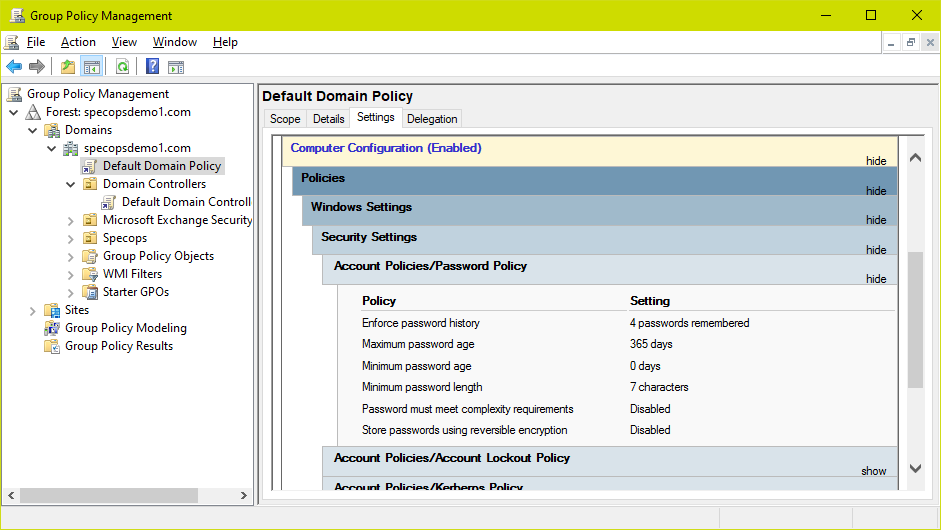 *image property of Specops Software* Deploying multi-factor authentication using tools such as RSA, Google Auth, etc is generally the next step and vastly hardens any system. **Change Management**  *image owned by Microsoft* Deploying changes is actually one of the easier versions of change control that you will find in IT Ops as it is primarily done by Windows themselves. Generally on "Patch Tuesday" Windows will deploy patches and updates to their security channel for download by their clients. These changes are Windows developed and tested which reduces the burden on in-house IT teams. Generally, when designing or auditing a change control, part of the core evidence that should be maintained is documentation showing successful testing. As Windows performs this step, all that is typically required of IT is ensuring that each patch is approved by appropriate management before being deployed. However, it is still best practice for server teams to test out new patches in a non production environment prior to production to see if the patch interferes with any custom configurations or applications running in the environment. Most importantly however, Microsoft will occasionally release critical patches which should be installed as soon as possible. These are most often to fix known, easily exploitable, vulnerabilities. As such, it is also important to develop a process for IT to push these critical patches before obtaining approval. Review after the fact is a common reasonable approach. To start compare patches currently installed to the Windows listing found [here](http://www.microsoft.com/technet/security/current.aspx). I hope by reading this you have a general idea of what types of security controls your company has in place to address these areas or have an idea of how to take care of them if not. Its always better to fix an issue before an auditor, regulator, or worse threat actor find them. Next week I will discuss the basics of securing Linux. Regards, Your friendly internet IT guy
| author | kotenoke |
|---|---|
| permlink | it-auditing-series-windows |
| category | it |
| json_metadata | "{"app":"peakd/2021.09.1","format":"markdown","description":"Short intro to Windows security","tags":["it","windows","security","audit","compliance"],"users":[],"image":["https://files.peakd.com/file/peakd-hive/kotenoke/23ynapajdhRfenaT1H4kQ4kkaHTrd1cGGsS8UuFwjiXRyaL9fppH5e2teYrZFhy2ARk7C.jpg","https://files.peakd.com/file/peakd-hive/kotenoke/23xf7Tx5p1gnyjK4s2onWeTAdzpzJAGfAqv5bZe2acKpkprTskTXEgGrhUf3xUPKaWh54.png","https://files.peakd.com/file/peakd-hive/kotenoke/23wXLgX4fjmVM4ZZw3wpy3Ykm39fTKMugFf9mMp3b1vZddCyB2ytuVFLnEdHaQbwf4QRX.png","https://files.peakd.com/file/peakd-hive/kotenoke/48Fi6mFbSMUQDg9jbS7hVC9eStJUaGvwPUF8t5Xqau7EsSS8GL245uyr7XwnsxRrfA.png"]}" |
| created | 2021-09-23 05:45:12 |
| last_update | 2021-09-23 05:45:12 |
| depth | 0 |
| children | 6 |
| last_payout | 2021-09-30 05:45:12 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.438 HBD |
| curator_payout_value | 0.433 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 6,421 |
| author_reputation | 11,024,215,753,635 |
| root_title | "IT Auditing Series - Windows" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 106,497,069 |
| net_rshares | 1,108,584,335,135 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| saltiberra | 0 | 1,208,142,126 | 10% | ||
| tryskele | 0 | 1,011,635,637 | 4% | ||
| trincowski | 0 | 74,050,350,343 | 20% | ||
| brittandjosie | 0 | 922,076,662,321 | 100% | ||
| canna-collective | 0 | 576,790,276 | 2% | ||
| oceanbee | 0 | 18,885,863,912 | 100% | ||
| anddumbcunts | 0 | -123,727,624 | -1% | ||
| vipservice | 0 | 2,973,754,884 | 2% | ||
| drew0 | 0 | 968,868,061 | 10% | ||
| rawnass | 0 | 3,979,919,161 | 100% | ||
| failingforwards | 0 | 77,596,779,593 | 100% | ||
| nina81 | 0 | 586,601,009 | 100% | ||
| sev-7 | 0 | 908,476,483 | 100% | ||
| evachin | 0 | 969,464,159 | 100% | ||
| kotenoke | 0 | 1,054,715,621 | 100% | ||
| ntstatus | 0 | 1,860,039,173 | 100% |
Your friendly it noob reader says thanks
| author | brittandjosie |
|---|---|
| permlink | re-kotenoke-qzvin6 |
| category | it |
| json_metadata | {"tags":["it"],"app":"peakd/2021.09.1"} |
| created | 2021-09-23 06:13:54 |
| last_update | 2021-09-23 06:13:54 |
| depth | 1 |
| children | 0 |
| last_payout | 2021-09-30 06:13:54 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 41 |
| author_reputation | 525,661,217,955,513 |
| root_title | "IT Auditing Series - Windows" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 106,497,491 |
| net_rshares | -4,095,036,653 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| spaminator | 0 | -5,115,044,913 | -0.25% | ||
| kotenoke | 0 | 1,020,008,260 | 100% |
Nobu looks so fluffy! and the post for this pic........ 😅😂😎
| author | evachin |
|---|---|
| permlink | re-kotenoke-r04hci |
| category | it |
| json_metadata | {"tags":["it"],"app":"peakd/2021.09.1"} |
| created | 2021-09-28 02:24:21 |
| last_update | 2021-09-28 02:24:21 |
| depth | 1 |
| children | 0 |
| last_payout | 2021-10-05 02:24:21 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 59 |
| author_reputation | 5,808,415,506,857 |
| root_title | "IT Auditing Series - Windows" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 106,614,478 |
| net_rshares | 0 |
hello, thank you for sharing this valuable information.
| author | nina81 |
|---|---|
| permlink | re-kotenoke-qzw4k5 |
| category | it |
| json_metadata | {"tags":["it"],"app":"peakd/2021.09.1"} |
| created | 2021-09-23 14:00:30 |
| last_update | 2021-09-23 14:00:30 |
| depth | 1 |
| children | 0 |
| last_payout | 2021-09-30 14:00:30 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 56 |
| author_reputation | 19,741,486,827,806 |
| root_title | "IT Auditing Series - Windows" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 106,505,169 |
| net_rshares | 0 |
This is indeed great information that I'm sure a lot of people are lacking and / or ignoring. I'm probably a little bit of both, though I do try and keep our home network and computers shielded. Hah - at work they are now implementing 2FA, can't blame them. I'm looking forward to your next post because I just installed Linus for the first time on an older Windows 10 laptop and am using that aside from my Win10 PC.
| author | oceanbee |
|---|---|
| permlink | re-kotenoke-qzwr0b |
| category | it |
| json_metadata | {"tags":["it"],"app":"peakd/2021.09.1"} |
| created | 2021-09-23 22:12:12 |
| last_update | 2021-09-23 22:12:12 |
| depth | 1 |
| children | 1 |
| last_payout | 2021-09-30 22:12:12 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 420 |
| author_reputation | 129,229,940,625,604 |
| root_title | "IT Auditing Series - Windows" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 106,514,922 |
| net_rshares | 1,058,184,036 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| kotenoke | 0 | 1,058,184,036 | 100% |
Very nice. Linux is used to support most company infrastructure outside of the Windows domain that end users interface with. Its a great OS to learn and the skills you'll pick up will transfer to learning CMD/Powershell in Windows.
| author | kotenoke |
|---|---|
| permlink | re-oceanbee-qzwxpa |
| category | it |
| json_metadata | {"tags":["it"],"app":"peakd/2021.09.1"} |
| created | 2021-09-24 00:36:48 |
| last_update | 2021-09-24 00:36:48 |
| depth | 2 |
| children | 0 |
| last_payout | 2021-10-01 00:36:48 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 232 |
| author_reputation | 11,024,215,753,635 |
| root_title | "IT Auditing Series - Windows" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 106,517,118 |
| net_rshares | 1,847,454,895 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| oceanbee | 0 | 1,847,454,895 | 10% | ||
| anddumbcunts | 0 | 0 | -0.1% |
Interesting post, thanks for sharing.
| author | trincowski |
|---|---|
| permlink | re-kotenoke-2021923t145042615z |
| category | it |
| json_metadata | {"tags":["it","windows","security","audit","compliance"],"app":"ecency/3.0.22-mobile","format":"markdown+html"} |
| created | 2021-09-23 13:50:42 |
| last_update | 2021-09-23 13:50:42 |
| depth | 1 |
| children | 0 |
| last_payout | 2021-09-30 13:50:42 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 38 |
| author_reputation | 159,418,145,168,851 |
| root_title | "IT Auditing Series - Windows" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 106,504,945 |
| net_rshares | 0 |
 hiveblocks
hiveblocks