<div class="text-justify">Greetings community steemit, today I share with you a very important publication that we must know, especially web developers, administrators and system maintainers; as they are the main attacks that can suffer the applications or Web sites. As we all know every day the technology presents significant changes, where there are many methods and tools that can harm our systems and web applications through multiple attacks. During the passage of time, the advance and technological development has grown exponentially, which until now knows no limits. In parallel, the knowledge and exploitation of the vulnerabilities of the systems has also grown to make them fall, or change the purpose for which they are created.
<br/>
There are techniques or methods that are used to attack a page or website, as well as servers. We will explain some common types of attacks that are carried out on websites and web servers.
What can we do with what you will know? Simple, to know how the attack works and thus avoid being the victim of a specific attack; to be able to defend ourselves or to shield our systems we must know how these attacks work, that is, to become attackers. Surely with this publication you will ask yourself: Is my Website ready for any attack? I do not want to sow doubt, the idea is to know and be able to achieve protection for your web resources.
<center>
[Source: Pixabay](https://pixabay.com/es/binaria-las-manos-teclado-grifo-2450152/)</center>
Many of these attacks have been created based on the weaknesses of the systems, to attack their vulnerabilities and although not all computer attacks are based on them, it is good to know which are the most used, to act against them.
## Below are some of the most known or most common attacks on websites or web applications and how they work:
### 1.- Injection by code attack:
<br/>
This type of attacks injects source code such as SQL, HTML to the website attacked, changing its original functionality or revealing data stored in the databases they use. Injection attacks, more specifically sqli (Structured Query Language Injection) is a technique to modify a database query string by injecting code into the query. The SQLI exploits a possible vulnerability where queries can be executed with the validated data.
SQL stands for Structured Query Language, allows us to access a database.
SQL can: execute queries against a database, retrieve data from a database, insert new records in a database, delete, records from a database and update records in a database.
<center>
Image edited by my author</center>
SQL Injection are still one of the most used website techniques and can be used to gain access to database tables, including user information and password. Sqli attacks are also among the easiest attacks to run, requiring no more than a single PC and a small amount of database knowledge.
***¡To keep in mind always!***
- The injection most times will be executed on a different server.
- The DB server may not even have Internet access.
<center>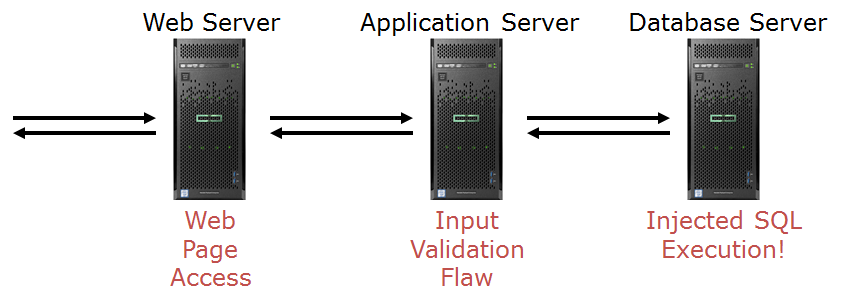
Image edited by my author</center>
<br/>
### 2.- Attack of Denial of Services or DDoS
<br/>
Denial of Service (DoS) or Denial of Distributed Service (DDoS) means that the server that hosts the web page from many computers is attacked so that it stops working correctly, causing an overload. The Denial of Service are the most common ways to freeze the operation of a website, that is, it is an attack technique whose objective is to prevent a website from allowing the usual activity of the users. These are the attempts to flood a site with external requests, that is multiple requests, so that site could not be available to users. Denial of service attacks usually target specific ports, IP ranges or complete networks, but can be directed to any particular connected device or service.
<center>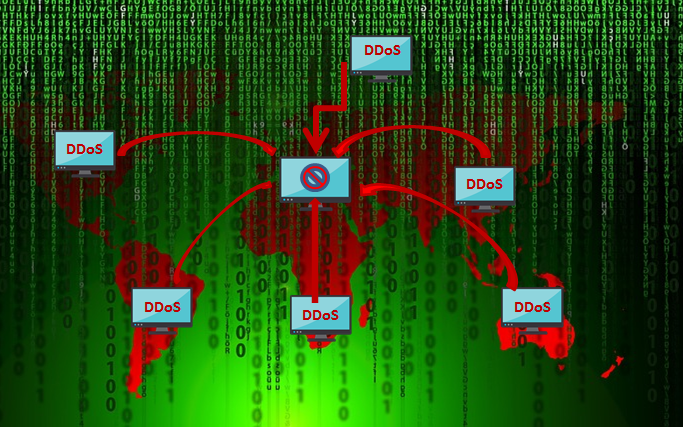
Image edited by my author</center>
Denial of service attacks work when a computer with an Internet connection tries to flood a server with packets. DDoS, on the other hand are when many devices, often widely distributed, in a botnet attempt to flood the target often with thousands of requests.
***DDoS attacks can be presented in 3 ways, which would be the main ones:***
- Volume attacks, where the attack attempts to overflow the bandwidth at a specific site.
- The protocol attacks, where the packets try to consume services or resources of the network.
- Attacks to applications, where requests are made with the intention of "exploiting" the web server, through the application layer.
<center>
[Source: Pixabay](https://pixabay.com/es/bomba-explosivos-detonaci%C3%B3n-154456/)</center>
<br/>
### 3.- Brute Force Attack
<br/>
A brute force attack is an automated trial and error process used to guess a username, password, credit card number or cryptographic key. This type of attack basically tries to "break" all possible combinations of username + password in a web page. Brute force attacks look for weak passwords to be deciphered and access easily. The attackers have good weather, so the trick is to make your passwords safe enough and the attacker would get tired before deciphering your password. As computers become more and more powerful the need to create stronger passwords becomes increasingly important.
<center>
[Source: Pixabay](https://pixabay.com/es/hacker-estafador-estafa-identidad-3081816/)</center>
<br/>
<div class="pull-right">https://cdn.steemitimages.com/DQmZS5kAvmK6wJxPKPRFXZbEjpEs5pk5pK4J5VB1WDb6uHe/image.png
<a href=https://pixabay.com/es/contrase%C3%B1a-palabra-clave-palabra-866981/>Source:Pixabay</a></center></div>
This attack can occur on any page that requires a login to enter, although today there are many techniques used to avoid it. Due to the popularity of this type of attacks we can find in many web sites the so-called captchas, which try to detect if the person trying to access the service is human is a computer software trying to burst a password.
<br/>
### 4.- Attacks of Cross-Site Scripting (XSS)
<br/>
This type of attack is based on inserting code or script on the website of the victim, and make the visitor to enter the site execute it and fulfill the purpose for which it was written, such as theft of sessions or vulnerable data. Attackers use Cross-site Scripting (XSS) to inject malicious scripts into what would be harmless websites. Because these scripts seem to come from trusted websites, the end-user's browser almost always executes the script, the hackers' concession, access to the information contained in the cookies or session tokens used with that site. The XSS is generally used to obtain access from a user of the account.
<center>
[Source: Pixabay](https://pixabay.com/es/de-seguridad-criptomoneda-bitcoin-2972105/)</center>
Cross-site Scripting or XSS allows attackers to execute scripts in the victim's browser, which can hijack user sessions, deface web sites, insert hostile content, perform phishing attacks and take over the browser. user through the use of malicious scripts. The malicious script is usually JavaScript, but any scripting language compatible with the victim's browser is a potential target for this attack.
### 5.- Buffer overflow
<br/>
A buffer overflow is a software error that occurs when a program does not adequately control the amount of data that is copied over a memory area reserved for that purpose (buffer), so that if that amount is greater than the assigned capacity the remaining bytes are stored in adjacent memory areas, overwriting their original content. This constitutes a programming failure.
<center>
[Source: Pixabay](https://pixabay.com/es/hombre-elegante-en-internet-red-1657004/)</center>
The exploitation of a buffer overflow is an attack that alters the flow of an application by overwriting parts of the memory. Buffer overflow attacks, also known as buffer overruns, are designed to trigger the execution of arbitrary code in a program by sending a greater amount of data than it can receive.
### 6.- Directory indexing
The indexing or automatic directory listing is a function of the web server that lists all the files of the requested directory if the usual startup file is not present.
### 7.- Information leakage
More than being an attack, it is an error of the administrator of the site, which consists of leaving public the registry of errors, which facilitates the attacker to see the exact faults of the system, take advantage of these, and obtain partial or total control of the system. site. Information leakage occurs when a website reveals sensitive information, such as comments from developers or error messages, that can help an attacker to exploit the system.
<center>
[Source: Pixabay](https://pixabay.com/es/matriz-binaria-seguridad-privado-2883622/)</center>
---
---
### These are some of the many types of attacks, all with the same objectives to make the systems fall, generate cyber terror, but above all usurp the information, looking for that which has value and represents a gain for the attacker. If you administer a website, it is necessary to make all possible security implementations to make life difficult for attackers, otherwise if you are an internet user, as well as in real life, you must be alert and careful not to be a victim of a computer attack.</div>
### References:
https://www.owasp.org/index.php/Category:Attack
https://www.owasp.org/index.php/Cross_Site_Scripting_Flaw
https://www.certsi.es/en/blog/owasp-publishes-top-10-2017-web-application-security-risks
<br/>
<center></center>
 hiveblocks
hiveblocks