**With blockchains, every public key can now have its own address.**

Source: https://sovrin.org/library/sovrin-protocol-and-token-white-paper/
This address is called a decentralized identifier (DID)—another standard coming from the W3C.
DIDs provide a standard way for individuals and organizations to create permanent, globally unique, cryptographically verifiable identifiers entirely under the identity owner’s control.
DID is not rented from any service provider, and no one can take it away from whomever owns or controls the associated private key.
DIDs are the first globally unique verifiable identifiers that require no registration authority.
A DID is stored on a blockchain along with a DID document containing the public key for the DID, any other public credentials the identity owner wishes to disclose, and the network addresses for interaction.
The identity owner controls the DID document by controlling the associated private key.
Because DIDs are an open standard, any blockchain can create a DID method defining how DIDs can be registered (written) and resolved (read) on that blockchain.
And because control over a DID is asserted entirely using cryptography—by digitally signing the transaction with the blockchain where the DID is registered—no central authority is needed to register the DID.
Nor is any central authority needed to track or manage DIDs.
DIDs enable true self-sovereign identity—lifetime portable digital identity for any person, organization, or thing that can never be taken away.
Furthermore, given the right blockchain economics, DIDs can be cheap, so people can generate as many as they need to protect their privacy.
Lastly, and most importantly, every person and organization with access to the Internet can have the means to prove their ownership of a public key, thereby enabling their claims to be verified.
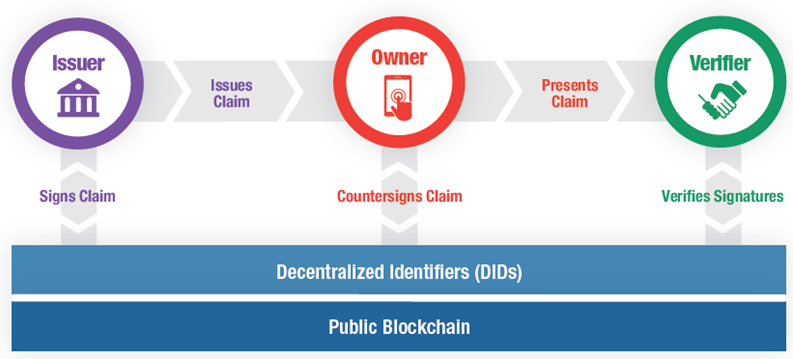
We can finally use the same process to verify identity online that we have been using offline for centuries. Because every DID has an associated public-private key pair, anyone with a DID should be able to digitally issue and sign verifiable claims and other documents.
So long as the verifier has the DID of the issuer (which in most cases is contained in the credential itself), it is a simple matter to look up the issuer’s public key on the blockchain and verify the signature on the claims.
With a public blockchain for DIDs, anyone can issue a digitally-signed credential, and anyone else can verify it Issuers and verifiers of digital credentials should no longer need to form identity federations.
The DID specification ensures that issuers and verifiers everywhere can look up
the necessary public keys on a public blockchain regardless of whether they belong to the same organization or identity federation.
This progression—from disconnected “islands of identity” each with its own PKI to a global identity network based a decentralized PKI (DPKI)—is the same progression that occurred in moving from “islands of networking” (local area networks) into the global Internet.
The starting point must be a public blockchain.
With a public key on a public blockchain, every identity owner can now be their own self-sovereign identity provider.
As Constellation Research analyst Stephen Wilson points out, this doesn’t mean that an identity owner controls every aspect of their identity.
Rather, as Sovrin Foundation Chair Phil Windley has written, self-sovereign identity is powerful because it clearly delineates the boundaries within which the identity owner has complete control, and outside of which the owner must form relationships with others.
For example, identity owners will need to work with other issuers of verifiable claims if they want to build trust in their identity.
They also recognized that they could not establish Sovrin alone. It had to be a community effort, just like every other core piece of Internet infrastructure.
Every facet of Sovrin architecture is designed to address the four major requirements of SSI: governance, scalability, accessibility, and privacy.
As the design of Sovrin progressed, Evernym and the other founders of the Sovrin Foundation realized that there were four overarching requirements to building a successful SSI system:
1. Governance: how the network can be trusted by all stakeholders.
2. Performance: how the network can provide self-sovereign identity at Internet scale.
3. Accessibility: how the network can ensure that identity is available to all.
4. Privacy: how the network can meet the strongest privacy standards in the world.
Sovrin governance is based on a universal trust framework for SSI(Self sovereign identity)
The principles of self-sovereign identity transcend any particular type of blockchain or distributed ledger.
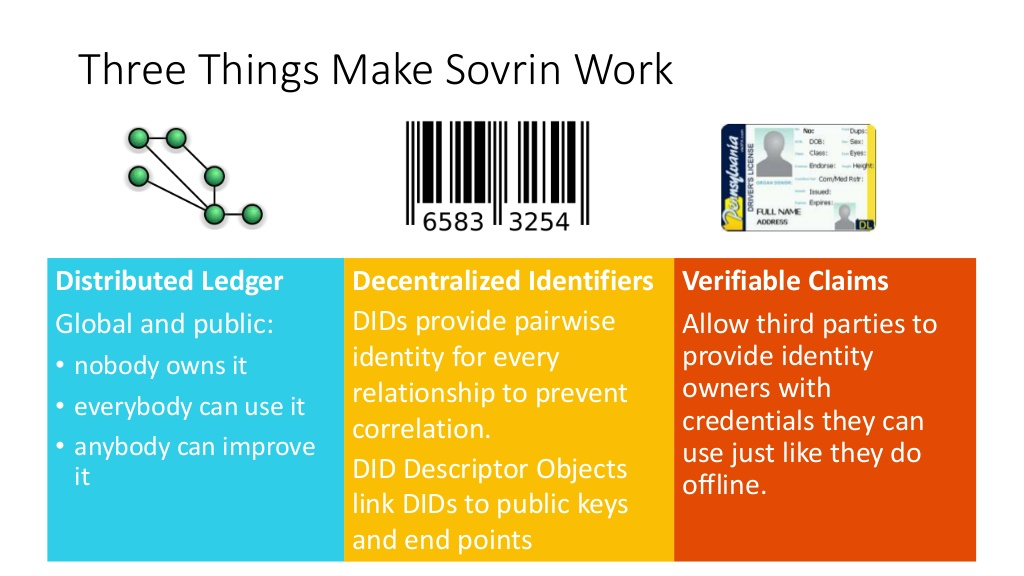
But SSI is not dependent on a particular type of blockchain distributed ledger technology (DLT)—it can work with any blockchain or DLT capable of meeting fundamental principles.
The first job of the Sovrin Foundation was to capture these principles in the Sovrin Trust Framework.
The Sovrin Trust Framework Working Group—composed of volunteer experts in digital identity, privacy, and policy from around the world—worked for eight months to develop the first trust framework that would provide the legal and policy foundation for a global public utility for SSI.
The network must have the performance and scalability of DNS
A global public utility for self-sovereign identity should be used even more than DNS.
Although the DNS is capable of much more, the vast majority of DNS requests are simply to look up the IP address for a domain name.
With over 1 billion host computers now available on the Internet, the DNS is serving over 100 billion lookups per day.
The same should be true of a global public utility for DIDs—only instead of looking up IP addresses from domain names, it will be looking up public keys from DIDs.
If you imagine every person, organization, or thing needs a collection of DIDs—one for every relationship they have—then it is easy to imagine that there could be trillions of DIDs in a global decentralized identity system.
Sovrin is explicitly designed to achieve this scale. DNS is simpler to scale (yet more susceptible to attack) because it does not use a consensus protocol to create an immutable blockchain.
Yet all consensus protocols can only scale to a limited number of validator nodes. To overcome this hurdle, the Sovrin Network is designed to use two rings of nodes:
a ring of validator nodes to accept write transactions, and a much larger ring of observer nodes running read-only copies of the blockchain to process read requests.
In addition, the Sovrin blockchain is engineered to be able to return a state proof with any response. This is a very lightweight cryptographic proof—capable of being processed on a smartphone—that the response is valid according to the current state of the ledger, which should prevent man-in-the-middle attacks on Sovrin queries.
As valuable as identity credentials are in the developed world—where they are so embedded in our everyday life that we often take them for granted—in many developing countries they can be the difference between life and death.
Child kidnapping, sex slavery, forced labor, and other forms of human trafficking all depend on the ability to prevent a person from being accurately identified.
Refugee systems around the world require identity solutions that must work in the harshest
conditions—and of course they must work beyond the boundaries of a single nation.
Just like with the Internet, cost should not be a barrier to access.
Universal access can be achieved in several ways: by running a public permissioned ledger at cost; by designing a very low-cost permissionless ledger; or by subsidizing the cost of SSI on any ledger.
At the heart of Sovrin architecture are three fundamental examples of “privacy as the default setting.”
1. Pseudonymity by default. Sovrin supports pairwise-unique DIDs and public keys.
2. Private agents by default. To prevent correlation, no private data is stored on the ledger, even in encrypted form.
3. Selective disclosure by default. Sovrin verifiable claims use cryptographic zero-knowledge proofs so they can automatically support data minimization.
Every universal identifier is a major correlation risk—even your mobile phone number.
Government ID numbers, credit card numbers, and phone numbers are all examples of universal identifiers. Universal identifiers allow your activity to be tracked everywhere you use them.
With today’s computer technology we don’t have to rely on this type of highly-correlatable identifier. They are a 20th century tool that is no longer appropriate for the digital age.
It is time we stopped using these outdated methods and started using technology that is designed to protect privacy without sacrificing functionality.
The solution is pairwise-pseudonymous identifiersaseparate DID for every relationship.
Imagine that when you open a new account with an online merchant, instead of giving them a credit card number or phone number, you gave them a DID created just for them.
They could still use this DID to contact you about your order, or to charge you a monthly subscription, but not for anything else.
If the merchant suffered a breach and your DID were compromised in any way, you would just cancel it and give them a new one—without affecting any other relationship.
The extraordinary consequence of this shift is that a pairwise-pseudonymous DID is not worth stealing. Not only can the criminal not use it anywhere else, but the moment either you or the merchant detects a problem, you simply can change the DID.
No private data is stored on the Sovrin ledger—even in an encrypted form—so it cannot be used for correlation An immutable public blockchain never forgets.
never put any private data on the ledger itself.Instead, put only pseudonymous identifiers (DIDs), pseudonymous public keys, and agent addresses (see below).
This enables the exchange of any private data to happen entirely off-ledger.
However the more immediate risk is that the private keys for the encrypted data—or the raw inputs to hashed data— are stolen or accidentally compromised.
Then this indelible, globally-replicated data record is revealed to all, forever. The solution is a P2P network of distributed private agents working in parallel with the distributed ledger.
In Sovrin architecture, each DID has a corresponding private agent—with ist own pseudonymous network address—from which the identity owner can exchange verifiable claims and any other data with another identity owner over an encrypted private channel.
As shown here, private agents can operate Sovrin enables selective disclosure of verifiable claims Selective disclosure lets identity owners control how much data is shared in a particular context.
The classic example is date of birth.
Selective disclosure uses a cryptographic techniqueknown as a zero-knowledge proof (ZKP).
Suppose you had a digital copy of your driver’s license in the form of a verifiable claim. You could then use a mobile app to present a zero-knowledge proof that you are old enough to drink.
The bartender could verify the proof using the public key of the issuer (similar to verifying a digital signature). But the bartender never learns (i.e., has “zero knowledge of”) your actual birth date.
A public blockchain for SSI makes it feasible to deploy ZKP as the default for all Sovrin
verifiable claims.
Like the Bitcoin and Ethereum tokens, the Sovrin token is an intrinsic component of this new network. Designed to enable value exchange with the same privacy-preserving properties of the Sovrin protocol for verifiable claims exchange, the Sovrin token aligns the incentives of issuers, identity owners, and verifiers everywhere to build value as they build trust.
It is an essential element of a decentralized identity network and all the security and privacy benefits that spring from it.
Most importantly, this new infrastructure can help restore our trust in the network we all rely on to power our global economy and connect our global society.
I hope you liked the read!
Best regards
Orlando
 hiveblocks
hiveblocks