<div class="pull-left">https://steemitimages.com/DQmaYH2iwMSeAem2YEPEbUtBYHH1WV4k4vaXVJDKhmgJM4L/image.png</div> We rely on encryption and passwords for all sorts of things. Anytime you make a purchase online or at a store with a card, encryption is involved. The encryption is achieved basically by multiplying two large prime numbers together and the resulting, very large number is extremely hard to factor into the original two numbers by a thief or a hacker and this makes your transaction secure. This is what is called a one-way function. The problem is that it now looks like quantum computers might be coming. I have made a few posts on quantum computers [here](https://steemit.com/steemstem/@procrastilearner/the-online-quantum-computer-that-you-can-use), [here](https://steemit.com/steemstem/@procrastilearner/all-about-qubits) and [here](https://steemit.com/physics/@procrastilearner/testing-the-quality-of-the-ibm-qubit-with-3072-actual-quantum-computer-runs). It's a very interesting topic so you might want to take a look. If quantum computers ever are fully developed they may be able to quickly factor those large numbers we use for encryption using something called [Shor's algorithm](https://en.wikipedia.org/wiki/Shor's_algorithm) and this would effectively render our modern encryption techniques obsolete. This could also render a lot of cryptocurrencies obsolete as well. <center>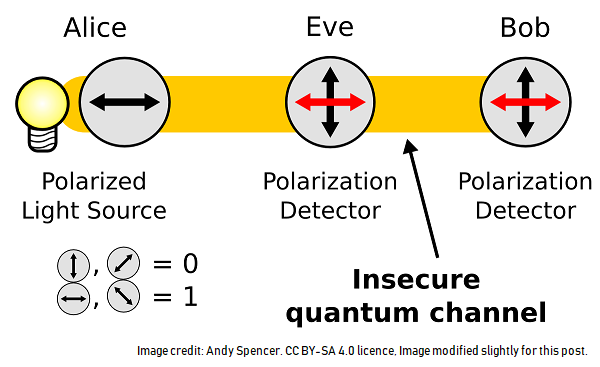</center> #### Quantum Cryptography To The Rescue Over 30 years ago a [scheme](https://en.wikipedia.org/wiki/Quantum_key_distribution#BB84_protocol:_Charles_H._Bennett_and_Gilles_Brassard_(1984)) to use the unique principles of quantum mechanics was developed to make it possible to create a secure one-time pad for later use in the encryption of a message. It goes as follows. * There are two polarization bases: one is vertical-horizontal and the other is where the polarizers are rotated by 45° * Photons that are polarized vertically are defined to represent 0. * Photons that are polarized horizontally are defined to represent 1. * Photons that are polarized at 45° are defined to represent 0. * Photons that are polarized at -45° are defined to represent 1. <center><b>Table 1. Quantum Cryptography Activity Sequences Explained</b></center> Activity Description | | | | | | | | | --|-- |-- |-- |-- |-- |-- |-- |-- | Alice's makes her random bits (this is kept secret)| 0 | 1 | 1 |0 |1 |0 |0 |1 | Alice's random sending polarization gate sequence (this is later shared)| + |+ |× |+ |× |× |× |+ | Photon polarization Alice sends| ↑|→|↘|↑|↘|↗| ↗|→| Bob's random measuring polarization gate sequence (this is later shared with Alice)| + |× |× |× |+ |×|+|+| Photon polarization Bob measures |↑|↗|↘ |↗|→|↗|→|→| Bit values that Bob measures (this is kept secret)|0|g|1|g|g|0|g|0| Public sharing of polarization gate sequences | Shared secret encryption key for one-time pad | 0 | |1 | | |0 | |1 | --- 'g' means 'garbage'. Due to quantum mechanics, Bob will measure a 0 or a 1 at random. He will save that data but later just through it away when the gate sequences are compared. The table above was adapted from [wikipedia.](https://en.wikipedia.org/wiki/Quantum_key_distribution#BB84_protocol:_Charles_H._Bennett_and_Gilles_Brassard_(1984)) It was modified by me to hopefully make it easier to understand. --- The list below in conjunction with the table above illustrate the activities for generating a one time pad using quantum mechanics: 1. Alice chooses a sequence of random bits. This is kept secret. 2. Alice then prepares a polarization sequence at random. This will later be shared with Bob. 3. Alice polarizes her light source, attenuates it down to a single photon and sends that photon over a communication channel to Bob. She does this over and over for each sequence. 4. Bob chooses a polarization sequence at random and uses that to measure each photon that Alice sends. 5. If Bob guesses the polarization correctly he will be able to correctly measure the photon that Alice sends. 6. If Bob guesses the polarization incorrectly he will just get a random answer from the incoming photon (see the Appendix at the end for an explanation). 7. Bob now has a sequence of digits but he can't use them for encryption just yet. 8. Bob sends his polarization sequence to Alice. It can be over a public channel, it really does not matter. I will explain that later. 9. Alice tells Bob which times he guessed correctly. 10. For all the gates that Bob guessed incorrectly, he just throws those bits away (the 'g' for garbage bits in my table). Alice does the same. 11. Alice and Bob now both have the same secure one-time pad from the bits they are left. These bits can now be used as a one time pad for encryption of a secret message. <div class="pull-left">https://steemitimages.com/DQmd3JzVGNw9R9uE9dFHfFjCpvzqaguYex859LreQHhaaRv/image.png</div> #### Eve Likes To Eavesdrop Okay, let's say that "evil Eve" is sitting in the middle, detecting these photons and using her polarizer to try to determine Alice's sequence. Quantum mechanics will not allow you to clone quantum states like this. Every measurement of a photon will destroy the original state. So Eve will therefore have to guess at what type of photon to send along to Bob after she measures and destroys Alice's original photon. Also, if Eve guesses the polarization wrong she will just be getting a random bit (0 or 1 at random) due to the nature of quantum mechanics (see Appendix for an explanation). She won't know it is random either, the photon won't "tell" her. Eve therefore has to send this random bit along to Bob and she will be wrong half the time. This means that the one-time pad that Bob generates at the end will be different than the one-time pad that Alice generates. When Alice encrypts her message and sends it to Bob, Bob will not be able to decrypt it and he will know right away that something went wrong. Eve will also have the wrong one time pad because the randomness of the incorrectly gated photons means her encryption sequence will be garbage. So, the nature of quantum mechanics makes this key generation technique very secure (when implemented correctly by the manufacturers). #### Closing Words What does this mean for us? Well one day quantum computers may make the keys for our cryptocurrencies vulnerable as well as for the encryption for our online banking and shopping. The nature of one-time pads is perfectly resistant to quantum computers because no algorithm was used in the making of the pad. This means that eventually we could see a new port on the back of our computers that is just for a fiber optic cable. This cable will run right into your house and to your computer's new port. The port and its associated chips will then be used to make one-time pads for your banking passwords and for your crptocurrency wallets. #### Appendix: Photon Polarization and Quantum Mechanics This little sequence of bullet points should illustrate the quantum nature of measuring polarized photons. * If you polarize a photon vertically and then send it through a polarizer that is vertical it will go right through it (100% of the time for a perfect polarizer). * If you polarize a photon vertically and then send it through a polarizer that is horizontal it will get stopped (100% of the time for a perfect polarizer). * If you polarize a photon vertically and then send it through a polarizer that is tilted at 45° only one-half of the time will it go through. The other half of the time it will get stopped. The effect is random and you never can know ahead of time which photon will make it and which photon will get stopped. When you polarize a photon vertically it's polarization can be best described not as 'up' but as 'up-like' or 'up-ish'. It will always go through a vertical polarizer but as you rotate that polarizer away from the vertical the odds of it going through decrease. It then becomes a matter of quantum chance if it makes through or not. At horizontal the odds drop right down to zero. *Thank you for reading my post.* </center> #### Post Sources A bit of the information was gathered from this [video.](https://www.youtube.com/watch?v=ToOLbdrWst4) as well as this Wikipedia [article.](https://en.wikipedia.org/wiki/Quantum_cryptography) and also this Wikipedia [article.](https://en.wikipedia.org/wiki/Quantum_key_distribution). The post's title was inspired by this [video.](https://www.youtube.com/watch?v=aKNzbB6a3mQ)
| author | procrastilearner |
|---|---|
| permlink | hey-can-i-speak-privately-with-you-an-intro-to-quantum-cryptography |
| category | steemstem |
| json_metadata | {"tags":["steemstem","physics","technology","steemeducation","technology-trail"],"image":["https://steemitimages.com/DQmaYH2iwMSeAem2YEPEbUtBYHH1WV4k4vaXVJDKhmgJM4L/image.png","https://steemitimages.com/DQmeBXEQeFe8NjMKk2gs8STw3UQGgyQSPLiVpFcZ9ExQUoZ/image.png","https://steemitimages.com/DQmd3JzVGNw9R9uE9dFHfFjCpvzqaguYex859LreQHhaaRv/image.png"],"links":["https://steemit.com/steemstem/@procrastilearner/the-online-quantum-computer-that-you-can-use","https://steemit.com/steemstem/@procrastilearner/all-about-qubits","https://steemit.com/physics/@procrastilearner/testing-the-quality-of-the-ibm-qubit-with-3072-actual-quantum-computer-runs","https://en.wikipedia.org/wiki/Shor's_algorithm","https://en.wikipedia.org/wiki/Quantum_key_distribution#BB84_protocol:_Charles_H._Bennett_and_Gilles_Brassard_(1984)","https://www.youtube.com/watch?v=ToOLbdrWst4","https://en.wikipedia.org/wiki/Quantum_cryptography","https://en.wikipedia.org/wiki/Quantum_key_distribution","https://www.youtube.com/watch?v=aKNzbB6a3mQ"],"app":"steemit/0.1","format":"markdown"} |
| created | 2018-03-27 01:35:03 |
| last_update | 2018-03-27 01:35:03 |
| depth | 0 |
| children | 5 |
| last_payout | 2018-04-03 01:35:03 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 13.203 HBD |
| curator_payout_value | 3.828 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 8,754 |
| author_reputation | 10,682,012,809,580 |
| root_title | "Hey, Can I Speak Privately With You? An Intro To Quantum Cryptography" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 0 |
| post_id | 46,801,019 |
| net_rshares | 6,789,861,127,124 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| pharesim | 0 | 79,460,348,600 | 0.05% | ||
| kushed | 0 | 9,271,207,258 | 7.19% | ||
| steem-id | 0 | 58,190,172,658 | 7.19% | ||
| mrs.agsexplorer | 0 | 45,853,812,410 | 10% | ||
| justtryme90 | 0 | 356,885,282,542 | 12.5% | ||
| anwenbaumeister | 0 | 168,129,584,662 | 7.19% | ||
| grandpere | 0 | 58,024,022,369 | 25% | ||
| liberosist | 0 | 329,500,011,719 | 7.19% | ||
| shaka | 0 | 374,174,726,705 | 10% | ||
| timsaid | 0 | 21,140,656,421 | 5% | ||
| velourex | 0 | 4,683,498,735 | 7.19% | ||
| lemouth | 0 | 111,066,451,978 | 25% | ||
| rjbauer85 | 0 | 1,195,852,166 | 25% | ||
| anarchyhasnogods | 0 | 41,521,407,983 | 12.5% | ||
| lamouthe | 0 | 5,848,689,970 | 25% | ||
| smasher | 0 | 575,135,627 | 10% | ||
| steemedia | 0 | 746,616,513 | 7.19% | ||
| meerkat | 0 | 175,856,288,266 | 7.19% | ||
| donchate | 0 | 464,772,226 | 5% | ||
| remlaps1 | 0 | 18,259,190,696 | 22% | ||
| saiku | 0 | 143,982,844 | 5% | ||
| curie | 0 | 285,156,029,167 | 7.19% | ||
| cebymaster | 0 | 930,355,610 | 7.19% | ||
| trueart | 0 | 841,293,436 | 5% | ||
| hendrikdegrote | 0 | 3,096,162,609,010 | 7.9% | ||
| steemstem | 0 | 667,170,944,865 | 25% | ||
| technology-trail | 0 | 6,559,816,648 | 100% | ||
| cotidiana | 0 | 831,207,122 | 7.19% | ||
| foundation | 0 | 2,382,834,800 | 25% | ||
| responsive | 0 | 147,794,717 | 7.19% | ||
| the-devil | 0 | 2,747,361,903 | 25% | ||
| thevenusproject | 0 | 13,487,805,974 | 25% | ||
| dna-replication | 0 | 10,904,720,637 | 40% | ||
| ihsan19 | 0 | 54,803,985 | 7.19% | ||
| lisa.palmer | 0 | 1,758,775,136 | 22% | ||
| lenin-mccarthy | 0 | 283,220,028 | 3.59% | ||
| dyancuex | 0 | 89,318,529 | 3.59% | ||
| borislavzlatanov | 0 | 2,011,891,209 | 25% | ||
| jamhuery | 0 | 4,047,216,639 | 25% | ||
| jdc | 0 | 53,304,772 | 0.71% | ||
| jacalf | 0 | 59,494,022 | 7.19% | ||
| oscarcc89 | 0 | 202,210,013 | 0.71% | ||
| kryzsec | 0 | 36,743,668,398 | 25% | ||
| markangeltrueman | 0 | 657,076,238 | 1.07% | ||
| nedspeaks | 0 | 5,197,153,035 | 25% | ||
| fredrikaa | 0 | 55,535,080,047 | 12.5% | ||
| odic3o1 | 0 | 55,258,563 | 2.5% | ||
| galberto | 0 | 287,293,315 | 0.21% | ||
| flurgx | 0 | 16,915,301,983 | 10% | ||
| tantawi | 0 | 675,988,925 | 7.19% | ||
| samminator | 0 | 8,566,725,965 | 25% | ||
| locikll | 0 | 2,742,290,106 | 14.38% | ||
| dber | 0 | 7,363,037,954 | 25% | ||
| mahdiyari | 0 | 1,615,940,497 | 2.15% | ||
| aboutyourbiz | 0 | 1,474,245,434 | 7.19% | ||
| dreamien | 0 | 417,755,940 | 7.19% | ||
| kerriknox | 0 | 82,958,475,308 | 25% | ||
| alexander.alexis | 0 | 1,438,711,672 | 5% | ||
| howtostartablog | 0 | 412,021,896 | 0.35% | ||
| sensation | 0 | 207,778,597 | 100% | ||
| zacherybinx | 0 | 56,189,255 | 7.19% | ||
| rockeynayak | 0 | 150,670,892 | 25% | ||
| ertwro | 0 | 10,251,080,485 | 25% | ||
| mystifact | 0 | 3,737,638,497 | 25% | ||
| coloringiship | 0 | 158,151,922 | 0.35% | ||
| juanjdiaz89 | 0 | 1,020,534,415 | 25% | ||
| nitesh9 | 0 | 6,117,005,081 | 25% | ||
| gambit.coin | 0 | 79,467,676 | 7.19% | ||
| himal | 0 | 1,888,712,867 | 25% | ||
| bachuslib | 0 | 21,087,066,182 | 100% | ||
| abigail-dantes | 0 | 414,475,557,979 | 25% | ||
| leczy | 0 | 1,925,310,869 | 25% | ||
| pkvlogs | 0 | 6,875,983,913 | 7.19% | ||
| ovij | 0 | 3,176,412,891 | 25% | ||
| joseg | 0 | 354,859,416 | 15% | ||
| planetenamek | 0 | 1,414,075,351 | 10% | ||
| mountain.phil28 | 0 | 711,075,193 | 7.5% | ||
| akeelsingh | 0 | 715,773,235 | 25% | ||
| somethingburger | 0 | 1,782,393,684 | 25% | ||
| tormiwah | 0 | 858,326,016 | 7.5% | ||
| infinitelearning | 0 | 231,649,504 | 3.59% | ||
| ponpase | 0 | 97,012,504 | 3.59% | ||
| ksolymosi | 0 | 4,096,588,941 | 25% | ||
| simplifylife | 0 | 3,610,035,784 | 12.5% | ||
| jordanx2 | 0 | 397,241,845 | 3.59% | ||
| thatterrioguy | 0 | 431,972,285 | 5.39% | ||
| birgitt | 0 | 206,470,079 | 7.19% | ||
| mayowadavid | 0 | 1,936,167,425 | 12.5% | ||
| zeeshan003 | 0 | 491,102,032 | 25% | ||
| markmorbidity | 0 | 57,244,201 | 3.59% | ||
| erodedthoughts | 0 | 648,482,908 | 1.25% | ||
| enzor | 0 | 448,464,922 | 12.5% | ||
| kieranpearson | 0 | 107,694,182 | 0.71% | ||
| bobdos | 0 | 435,972,973 | 0.71% | ||
| carloserp-2000 | 0 | 4,233,109,978 | 25% | ||
| rachelsmantra | 0 | 1,051,339,503 | 25% | ||
| altherion | 0 | 10,511,823,166 | 25% | ||
| cryptotradingfr | 0 | 89,249,696 | 1% | ||
| gra | 0 | 9,189,212,029 | 25% | ||
| ifartrainbows | 0 | 174,832,326 | 6.25% | ||
| sci-guy | 0 | 62,911,787 | 25% | ||
| delph-in-holland | 0 | 84,375,182 | 3.59% | ||
| spectrums | 0 | 347,412,586 | 7.19% | ||
| aboutcoolscience | 0 | 20,650,002,715 | 20% | ||
| aehiguese | 0 | 59,110,135 | 7.19% | ||
| skycae | 0 | 1,843,574,975 | 7.19% | ||
| xanderslee | 0 | 441,371,197 | 7.19% | ||
| otsouvalas | 0 | 1,506,171,056 | 7.19% | ||
| kenadis | 0 | 6,635,688,279 | 25% | ||
| esaia.mystic | 0 | 363,118,057 | 7.19% | ||
| amavi | 0 | 3,867,749,647 | 5% | ||
| robotics101 | 0 | 916,415,704 | 20% | ||
| jaeydallah | 0 | 101,290,876 | 7.19% | ||
| gentleshaid | 0 | 4,356,210,025 | 25% | ||
| crescendoofpeace | 0 | 77,769,791 | 3.59% | ||
| cgbartow | 0 | 1,056,769,574 | 12.5% | ||
| tito36 | 0 | 53,021,253 | 7.19% | ||
| adetola | 0 | 626,415,668 | 25% | ||
| dysfunctional | 0 | 948,540,701 | 12.5% | ||
| thedrewshow | 0 | 50,497,448 | 7.19% | ||
| speaklife | 0 | 89,604,803 | 7.19% | ||
| wanderingdanish | 0 | 249,439,836 | 1% | ||
| jlmol7 | 0 | 76,528,662 | 12.5% | ||
| hadji | 0 | 1,191,288,772 | 25% | ||
| sakura1012 | 0 | 454,969,700 | 25% | ||
| haarshan36 | 0 | 149,768,926 | 7.19% | ||
| fidelpoet | 0 | 290,204,261 | 7.19% | ||
| terrylovejoy | 0 | 1,529,671,805 | 5% | ||
| victoryudofia | 0 | 118,401,032 | 7.19% | ||
| wisewoof | 0 | 878,728,677 | 3.59% | ||
| neneandy | 0 | 197,477,992 | 4.31% | ||
| debbietiyan | 0 | 128,739,838 | 3.59% | ||
| singhbinod08 | 0 | 96,024,493 | 25% | ||
| rionpistorius | 0 | 466,014,418 | 12.5% | ||
| randomwanderings | 0 | 228,366,593 | 7.19% | ||
| deutsch-boost | 0 | 369,567,145 | 20% | ||
| caitycat | 0 | 131,697,772 | 3.59% | ||
| dexterdev | 0 | 5,194,187,206 | 25% | ||
| ugonma | 0 | 347,696,373 | 25% | ||
| ameliabartlett | 0 | 115,881,840 | 0.53% | ||
| mindscapephotos | 0 | 92,201,562 | 2.51% | ||
| ajpacheco1610 | 0 | 138,385,926 | 12.5% | ||
| kimp0gi | 0 | 82,339,236 | 7.19% | ||
| drkomoo | 0 | 297,935,808 | 25% | ||
| procrastilearner | 0 | 24,304,850,584 | 100% | ||
| giovaabbatichio | 0 | 582,682,003 | 100% | ||
| wiredelta | 0 | 615,443,567 | 100% | ||
| chimtivers96 | 0 | 401,368,586 | 7.19% | ||
| zipporah | 0 | 484,156,705 | 1.43% | ||
| wrpx | 0 | 53,122,348 | 3.59% | ||
| jaycem | 0 | 55,349,165 | 9% | ||
| theunlimited | 0 | 51,165,552 | 10% | ||
| pseudojew | 0 | 411,767,501 | 25% | ||
| blerdrage | 0 | 145,230,532 | 3.59% | ||
| effofex | 0 | 114,133,397 | 12.5% | ||
| beograd | 0 | 1,294,568,664 | 100% | ||
| count-antonio | 0 | 64,531,704 | 12.5% | ||
| de-stem | 0 | 6,464,909,667 | 15% | ||
| hatuvera | 0 | 51,786,066 | 10% | ||
| irelandscape | 0 | 1,050,701,052 | 100% | ||
| chloroform | 0 | 501,463,941 | 25% | ||
| beautyinscience | 0 | 76,564,024 | 12.5% | ||
| star-vc | 0 | 150,007,196 | 25% | ||
| thecosmic.gamble | 0 | 603,308,993 | 100% |
Thank you for a very informative post. For all those wanting to learn more about this and the history of cryptography, I highly recommend reading [The Code Book](https://simonsingh.net/books/the-code-book/) by Simon Singh.
| author | irelandscape |
|---|---|
| permlink | re-procrastilearner-hey-can-i-speak-privately-with-you-an-intro-to-quantum-cryptography-20180327t112239729z |
| category | steemstem |
| json_metadata | {"tags":["steemstem"],"links":["https://simonsingh.net/books/the-code-book/"],"app":"steemit/0.1"} |
| created | 2018-03-27 11:22:39 |
| last_update | 2018-03-27 11:22:39 |
| depth | 1 |
| children | 1 |
| last_payout | 2018-04-03 11:22:39 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.020 HBD |
| curator_payout_value | 0.006 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 222 |
| author_reputation | 15,380,678,988,494 |
| root_title | "Hey, Can I Speak Privately With You? An Intro To Quantum Cryptography" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 46,876,607 |
| net_rshares | 10,825,596,105 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| procrastilearner | 0 | 10,825,596,105 | 48% |
Yeah, I read that book a while ago. I second that opinion.
| author | procrastilearner |
|---|---|
| permlink | re-irelandscape-re-procrastilearner-hey-can-i-speak-privately-with-you-an-intro-to-quantum-cryptography-20180327t153144439z |
| category | steemstem |
| json_metadata | {"tags":["steemstem"],"app":"steemit/0.1"} |
| created | 2018-03-27 15:31:45 |
| last_update | 2018-03-27 15:31:45 |
| depth | 2 |
| children | 0 |
| last_payout | 2018-04-03 15:31:45 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 58 |
| author_reputation | 10,682,012,809,580 |
| root_title | "Hey, Can I Speak Privately With You? An Intro To Quantum Cryptography" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 46,918,419 |
| net_rshares | 0 |
This was a very clear explanation. I really liked it :)
| author | lemouth |
|---|---|
| permlink | re-procrastilearner-hey-can-i-speak-privately-with-you-an-intro-to-quantum-cryptography-20180327t071417591z |
| category | steemstem |
| json_metadata | {"tags":["steemstem"],"app":"steemit/0.1"} |
| created | 2018-03-27 07:14:18 |
| last_update | 2018-03-27 07:14:18 |
| depth | 1 |
| children | 2 |
| last_payout | 2018-04-03 07:14:18 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.020 HBD |
| curator_payout_value | 0.006 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 55 |
| author_reputation | 338,011,164,701,274 |
| root_title | "Hey, Can I Speak Privately With You? An Intro To Quantum Cryptography" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 46,843,153 |
| net_rshares | 10,956,024,973 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| procrastilearner | 0 | 10,956,024,973 | 48% |
Thanks. My schtick is that I try to translate the difficult and technical STEM topics so that the average guy on the street can understand it. Well that's the idea.
| author | procrastilearner |
|---|---|
| permlink | re-lemouth-re-procrastilearner-hey-can-i-speak-privately-with-you-an-intro-to-quantum-cryptography-20180327t153644176z |
| category | steemstem |
| json_metadata | {"tags":["steemstem"],"app":"steemit/0.1"} |
| created | 2018-03-27 15:36:48 |
| last_update | 2018-03-27 15:36:48 |
| depth | 2 |
| children | 1 |
| last_payout | 2018-04-03 15:36:48 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 165 |
| author_reputation | 10,682,012,809,580 |
| root_title | "Hey, Can I Speak Privately With You? An Intro To Quantum Cryptography" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 46,919,318 |
| net_rshares | 0 |
We will like it for sure ^^
| author | lemouth |
|---|---|
| permlink | re-procrastilearner-re-lemouth-re-procrastilearner-hey-can-i-speak-privately-with-you-an-intro-to-quantum-cryptography-20180327t214326371z |
| category | steemstem |
| json_metadata | {"tags":["steemstem"],"app":"steemit/0.1"} |
| created | 2018-03-27 21:43:27 |
| last_update | 2018-03-27 21:43:27 |
| depth | 3 |
| children | 0 |
| last_payout | 2018-04-03 21:43:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.024 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 27 |
| author_reputation | 338,011,164,701,274 |
| root_title | "Hey, Can I Speak Privately With You? An Intro To Quantum Cryptography" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 46,974,953 |
| net_rshares | 9,651,736,286 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| procrastilearner | 0 | 9,651,736,286 | 41% |
 hiveblocks
hiveblocks