Salutations Steemians,
In this post I'm going discuss what phishing is, why it exists, and also give you some tips to avoid being phished. Considering the amount of value the Steem platform is generating, I think it's likely we could see phishing attacks attempting to capture the credentials of Steemit users. I'll also discuss a free tool my employer just launched to the public today that can be used to simulate phishing attacks and assess how at-risk your organization is to phishing, and the potential impact of a data breach.

[*Image source*](https://duo.com/blog/introducing-the-access-of-evil)
## What is phishing?
Phishing is a social engineering attack that exploits people's willingness to click on links, open attachments, or approve permissions in order to deliver drive-by malware or trick people into giving up their account credentials. Phishing is an especially effective method of compromising accounts, and it works because it takes advantage of human factors, such as greed, fear, curiosity, and human error in order to trick people into giving up the goods.
A targeted phishing attack that is crafted to breach a specific person is known as spear phishing.
## How can you identify a phishing attack?
The best behavior to adopt in order to mitigate phishing is to **always check the URL domain**. You can do this by hovering over the link, then verifying the domain isn't different by looking in the bottom left corner of your browser. The most common phishing vectors are email and social media messaging. A swath of different phishing approaches exist. Next, I'll go over a few of the major types.
### Impersonation

Image source: Phishme
On the internet, people aren't always who they say they are. It's okay to trust, but always verify! Just because your email client tells you an email was sent from someone, doesn't necessarily mean that it was. It's possible to spoof the sender's information to trick people into believing they are receiving an email from someone that they trust.
### Disguise
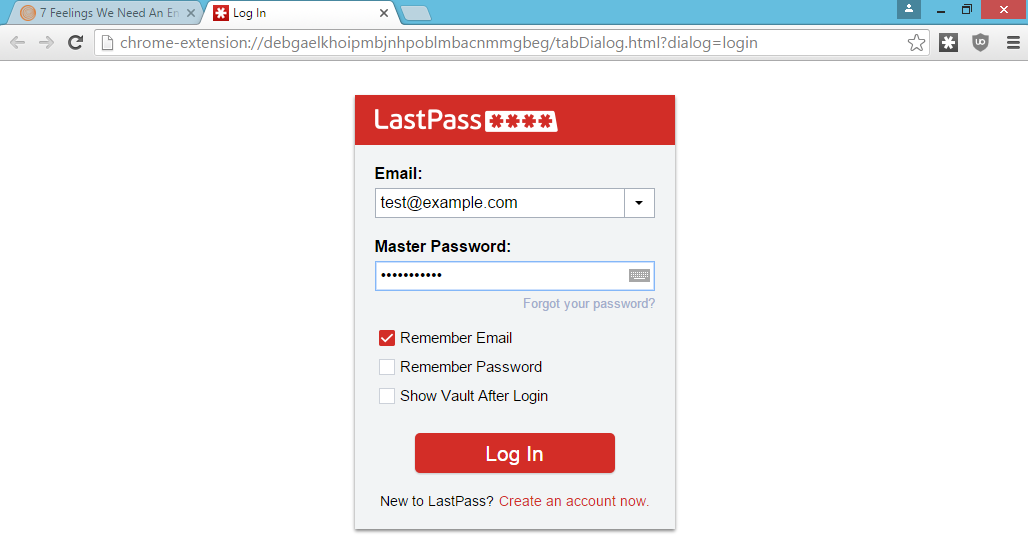
LastPass
LostPass
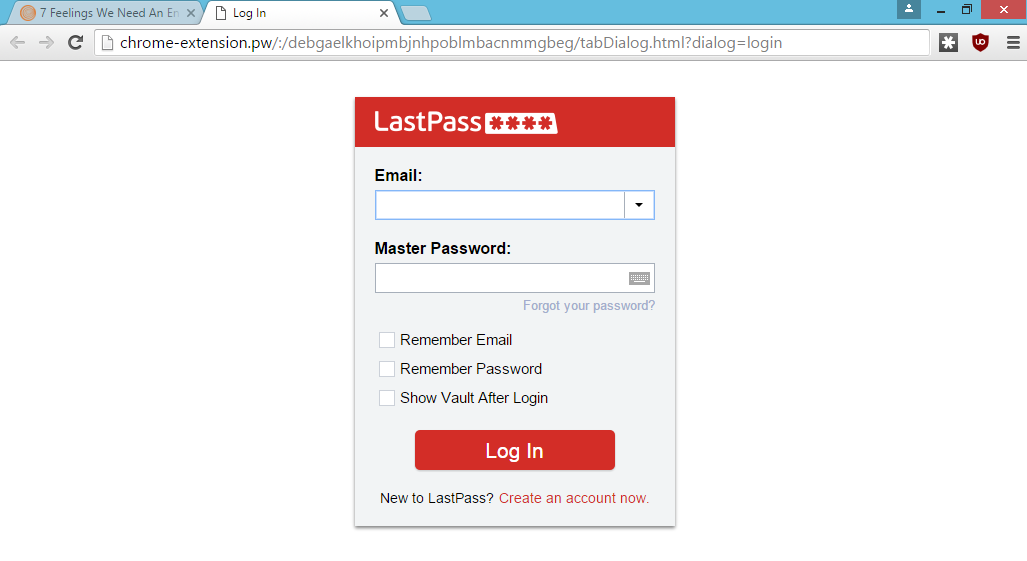
Many phishing pages look exactly the same as a trusted page. This password manager phish is very convincing. Can you spot the difference? This is a common method used to capture credentials by impersonating login pages.
### Ransomware

Don't download attachments that you don't expect without verifying authenticity out of band, even if they appear to originate from people you trust. They could encrypt your files and hold your data for ransom!
These are just a few examples, there are many others.
## Tips and tricks to prevent succumbing to a phishing attack
1. Employ a [web of trust extension](https://www.mywot.com/) to provide a signal as to the authenticity of a website.
2. Always double check the URL domain of websites before you visit them. Watch out for domains that are intended to look similar to a real domain, but are actually fake. Some techniques that these domains employ include:
* **Bitsquatting**, which anticipates a small portion of systems encountering hardware errors, resulting in the mutation of the resolved domain name by 1 bit. (e.g., zteemit.com).
* **Homoglyph**, which replaces a letter in the domain name with letters that look similar (e.g., steernit.com).
* **Repetition**, which repeats one of the letters in the domain name (e.g., steemiit.com).
* **Transposition**, which swaps two letters within the domain name (e.g., tseemit.com).
* **Replacement**, which replaces one of the letters in the domain name, perhaps with a letter in proximity of the original letter on the keyboard (e.g, steenit.com).
* **Omission**, which removes one of the letters from the domain name (e.g., stemit.com).
* **Insertion**, which inserts a letter into the domain name (e.g., steeemit.com).
* **Missing dot**, which removes a dot from the domain name (e.g., steemitcom.com).
* **Singularization or Pluralization**, which adds or removes “s” at the end of the domain name (e.g., steemits.com).
* **Vowel swap**, which replaces a vowel within the domain name (e.g., steamit.com).
* **Wrong TLD**, which replaces the top-level domain suffix (e.g., steemit.co).
[Read more about domain variations](https://zeltser.com/domain-name-variations-in-phishing/)
3. Sound the alarm. If you detect a phishing attack, tell others in your organization so they can avoid it.
4. Use [DMARC](https://dmarc.org/) to prevent your domains from being used in a phishing attack.
5. If you're prompted for account permissions, double check that you're on the proper website.
6. Beware of emails that sound too good to be true (No, you didn't really win $10,000 and you aren't really going to get a free annual gym membership).
7. Keep your browser software up to date to patch it against the latest security vulnerabilities. Chrome tries to automatically handle this for you (sometimes you need to go to Settings > About Chrome to complete the update).
8. Un-install browser plugins, such as Flash and Java, that have a [history](https://helpx.adobe.com/security/products/flash-player.html) of being vulnerable. This reduces the likelihood of installing drive-by malware by a lot!
## Quantify how at-risk your company is to phishing with Duo Insight
Duo has just launched [Insight](https://insight.duo.com/) to the public, which is a free tool that allows companies to assess how susceptible they are to data breach by means of phishing. This tool makes it quick and easy to set up a phishing campaign, and the quantitative report it provides is a good way to build a case for implementing stronger security controls and practices in your organization. We'd love to hear your feedback about this tool. You can read more about it [here](https://duo.com/blog/now-available-duo-insight-a-tool-to-help-organizations-identify-phishing-risks). Duo Insight does not store any credentials captured during phishing campaigns.
**DISCLAIMER: I work for Duo, but my personal opinions on Steemit.com are not representative of Duo's views. This post is intended to inform the Steemit community of a potential attack vector they may face in the future.**
#steemit #phishing #duo| author | robrigo |
|---|---|
| permlink | the-what-and-why-of-phishing-and-how-to-avoid-it |
| category | security |
| json_metadata | {"tags":["security","steemit","phishing","duo"],"image":["https://ipfs.pics/ipfs/QmWjfdT3w9mSsc6mdKSuZjykN3GUoqRVTbtFDbWwbWu5N8"]} |
| created | 2016-07-12 20:34:45 |
| last_update | 2016-07-12 20:38:12 |
| depth | 0 |
| children | 7 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 3.184 HBD |
| curator_payout_value | 0.435 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 6,588 |
| author_reputation | 36,085,196,360,202 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 88,009 |
| net_rshares | 9,307,870,215,226 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| anonymous | 0 | 801,717,913,286 | 100% | ||
| roadscape | 0 | 5,356,601,381,479 | 100% | ||
| tuck-fheman | 0 | 639,308,418,554 | 100% | ||
| donkeypong | 0 | 2,321,841,512,060 | 100% | ||
| konelectric | 0 | 2,337,613,114 | 100% | ||
| cryptorune | 0 | 673,048,063 | 100% | ||
| forrestwillie | 0 | 102,502,249,576 | 100% | ||
| acidyo | 0 | 484,947,347 | 100% | ||
| oholiab | 0 | 13,811,884,858 | 100% | ||
| thread | 0 | 2,987,609,506 | 100% | ||
| entropyjs | 0 | 22,392,632,279 | 100% | ||
| michaelx | 0 | 12,298,682,447 | 100% | ||
| graystone | 0 | 1,256,351,338 | 100% | ||
| riscadox | 0 | 86,924,063 | 100% | ||
| robrigo | 0 | 20,273,933,889 | 100% | ||
| matt-a | 0 | 1,925,095,143 | 100% | ||
| r4fken | 0 | 4,147,297,226 | 100% | ||
| katz | 0 | 167,992,904 | 100% | ||
| murderistic | 0 | 185,945,825 | 100% | ||
| juliano | 0 | -212,170,056 | -100% | ||
| chrisczub | 0 | 241,708,545 | 100% | ||
| condra | 0 | 2,616,984,837 | 100% | ||
| breathe3000 | 0 | 42,868,953 | 100% | ||
| csrolex | 0 | 42,032,509 | 100% | ||
| tjpezlo | 0 | 93,347,178 | 100% | ||
| isaackola | 0 | 44,010,303 | 100% |
Just discovered this post. I'm going to link it as "further reading" in my latest post about phishing. https://steemit.com/steemit/@condra/public-wallets-and-the-target-on-your-back-original-article I do think phishing represents a huge challenge for Steemit and crypto going forward.
| author | condra |
|---|---|
| permlink | re-robrigo-the-what-and-why-of-phishing-and-how-to-avoid-it-20160725t024208539z |
| category | security |
| json_metadata | {"tags":["security"],"links":["https://steemit.com/steemit/@condra/public-wallets-and-the-target-on-your-back-original-article"]} |
| created | 2016-07-25 02:41:57 |
| last_update | 2016-07-25 02:41:57 |
| depth | 1 |
| children | 0 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.020 HBD |
| curator_payout_value | 0.007 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 287 |
| author_reputation | 56,189,611,335,832 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 337,297 |
| net_rshares | 23,647,335,253 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| robrigo | 0 | 23,647,335,253 | 100% |
Excellent post and full of great info as always @robrigo !!! Here are some posts to help you get more traction and exposure to your Steemit posts, startup, business or self: **[[HOW TO] Public Relations Training For Startups, Steemers & Steemit: PART 1](https://steemit.com/public/@michaelx/public-relations-training-for-steemers-and-steemit)** **[[HOW TO] Public Relations Training For Startups, Steemers & Steemit: PART 2](https://steemit.com/marketing/@michaelx/public-relations-training-for-startups-steemers-and-steemit-part-2)** **[[HOW TO] Public Relations Training For Startups, Steemers & Steemit: PART 3](https://steemit.com/marketing/@michaelx/how-to-public-relations-training-for-startups-steemers-and-steemit-part-3)** Please let me know if there is anything I can do to help you become more successful! Oh and followed you too!
| author | michaelx |
|---|---|
| permlink | re-robrigo-the-what-and-why-of-phishing-and-how-to-avoid-it-20160712t203635415z |
| category | security |
| json_metadata | {"tags":["security"],"users":["robrigo"],"links":["https://steemit.com/public/@michaelx/public-relations-training-for-steemers-and-steemit"]} |
| created | 2016-07-12 20:36:24 |
| last_update | 2016-07-12 20:36:48 |
| depth | 1 |
| children | 2 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 847 |
| author_reputation | 10,068,003,664,289 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 88,019 |
| net_rshares | 23,497,953,152 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| thread | 0 | 2,929,028,928 | 100% | ||
| robrigo | 0 | 20,273,933,889 | 100% | ||
| murderistic | 0 | 181,177,984 | 100% | ||
| dougcrowe | 0 | 76,844,118 | 100% | ||
| usnewspress | 0 | 36,968,233 | 100% |
Thank you @michaelx. I'll give your articles a read this evening.
| author | robrigo |
|---|---|
| permlink | re-michaelx-re-robrigo-the-what-and-why-of-phishing-and-how-to-avoid-it-20160712t205507094z |
| category | security |
| json_metadata | {"tags":["security"]} |
| created | 2016-07-12 20:55:06 |
| last_update | 2016-07-12 20:55:06 |
| depth | 2 |
| children | 1 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 65 |
| author_reputation | 36,085,196,360,202 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 88,166 |
| net_rshares | 0 |
Thank you sir. Good to see you from the BTS forum. If you don't put a space after you @robrigo tag someone it won't work currently for some punctuation.
| author | michaelx |
|---|---|
| permlink | re-robrigo-re-michaelx-re-robrigo-the-what-and-why-of-phishing-and-how-to-avoid-it-20160713t003319932z |
| category | security |
| json_metadata | {"tags":["security"],"users":["robrigo"]} |
| created | 2016-07-13 00:33:09 |
| last_update | 2016-07-13 00:33:45 |
| depth | 3 |
| children | 0 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 156 |
| author_reputation | 10,068,003,664,289 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 89,250 |
| net_rshares | 116,140,960 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| dougcrowe | 0 | 79,172,727 | 100% | ||
| usnewspress | 0 | 36,968,233 | 100% |
That chrome-extension phish is a really nasty one and was probably super easy to do... chrome should totally be adding some builtin protection for things like that because it's particularly insidious. They should probably have a CA and associated cert generated by the browser in-memory on each startup to sign all local pages which will display a special padlock indicator so you at least have a visual prompt for when you're not on your actual settings pages. Or something more sensible.
| author | oholiab |
|---|---|
| permlink | re-robrigo-the-what-and-why-of-phishing-and-how-to-avoid-it-20160713t112456984z |
| category | security |
| json_metadata | {"tags":["security"]} |
| created | 2016-07-13 11:24:54 |
| last_update | 2016-07-13 11:24:54 |
| depth | 1 |
| children | 1 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 491 |
| author_reputation | 1,894,810,279,063 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 94,128 |
| net_rshares | 42,523,567,860 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| entropyjs | 0 | 22,392,632,279 | 100% | ||
| robrigo | 0 | 20,130,935,581 | 100% |
Agreed, thankfully LastPass has taken some steps to make it harder to pull off.
| author | robrigo |
|---|---|
| permlink | re-oholiab-re-robrigo-the-what-and-why-of-phishing-and-how-to-avoid-it-20160713t145614217z |
| category | security |
| json_metadata | {"tags":["security"]} |
| created | 2016-07-13 14:56:15 |
| last_update | 2016-07-13 14:56:15 |
| depth | 2 |
| children | 0 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 79 |
| author_reputation | 36,085,196,360,202 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 96,042 |
| net_rshares | 0 |
| author | tjpezlo |
|---|---|
| permlink | re-robrigo-the-what-and-why-of-phishing-and-how-to-avoid-it-20160726t175040656z |
| category | security |
| json_metadata | {"tags":["security"]} |
| created | 2016-07-26 17:50:45 |
| last_update | 2016-07-26 17:50:45 |
| depth | 1 |
| children | 0 |
| last_payout | 2016-08-25 04:02:27 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 49 |
| author_reputation | 11,144,454,418,634 |
| root_title | "The What and Why of Phishing, and How to Avoid It" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 380,075 |
| net_rshares | 29,306,665,001 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| robrigo | 0 | 29,213,317,823 | 100% | ||
| tjpezlo | 0 | 93,347,178 | 100% |
 hiveblocks
hiveblocks