<center>

</center>
Have you ever wanted to send a secret message to a friend, one that only they could understand? On the internet, when your computer talks to a website, it's sending messages back and forth. Just like your secret message, you wouldn't want anyone else to be able to read this information, especially if it's something private like your password or credit card details. This is where TLS comes in. Think of TLS as a secret code, a special language that only your computer and the website can understand, ensuring that all the information shared remains private.
Imagine you're sending that secret message in an envelope. TLS is like a special lock you put on that envelope. When you send it, it's all wrapped up securely so that only your friend, the website in this case, has the special key to unlock it and read what's inside. Another way to picture it is like a secret handshake. Before your computer and the website start sharing information, they do this special handshake to make sure they both trust each other. This handshake sets up the secret code they'll use for all their future conversations.
# What Exactly is TLS? Keeping the Bad Guys Out
TLS stands for Transport Layer Security. It's like a more modern and secure version of an older system called SSL, which stands for Secure Sockets Layer. You'll often hear people use these terms interchangeably, and when you see "HTTPS" at the beginning of a website address, that "S" means the website is using TLS (or sometimes still SSL) to keep your connection secure. The transition from SSL to TLS represents an evolution towards stronger security practices, but the older term "SSL" persists in common usage.
Why is this important? Well, TLS has a few key benefits. First, it keeps your information confidential. When you browse a website that uses TLS, all the data exchanged between your computer and the website is encrypted, meaning it's scrambled into a secret code. This prevents anyone else on the internet from eavesdropping and stealing your sensitive information like passwords, credit card numbers, or personal messages. Second, TLS helps with authentication. It makes sure that you're actually talking to the real website you intended to visit and not a fake one trying to trick you. This verification process builds trust in the connection. Finally, TLS ensures data integrity. It guarantees that the information sent between your computer and the website hasn't been tampered with or altered during its journey.
Let's go back to our secret message analogy. TLS makes sure the envelope is locked so no one can read it (confidentiality). It also verifies that the message is being delivered to the right person and not an imposter (authentication). And it ensures that the message inside hasn't been opened and changed by someone else along the way (integrity). These three elements are fundamental to secure online communication.
# Traefik: Your Website's Smart Gatekeeper
Now, let's talk about Traefik. Imagine Traefik as a very efficient and intelligent traffic controller for your website. When someone tries to visit your website, their request first goes to Traefik. Traefik then figures out where that request needs to go among your various web applications. One of the crucial roles Traefik plays is in managing security, and this is where TLS comes into the picture. Traefik can handle the secure connection (HTTPS) for all your websites and applications.
When Traefik is configured to handle TLS, it takes on the responsibility of the "secret code" part of the communication. This means your actual web applications don't need to worry about the complexities of encrypting and decrypting data. Traefik handles the secure connection, decrypts the incoming requests, and then forwards them to your applications. This process is known as TLS termination, and it simplifies the security setup for your web services.
# Putting Up Stronger Locks: Understanding TLS Options in Traefik
Traefik offers a great deal of flexibility in how it manages these secure connections. It allows you to customize the behavior of TLS through various settings known as "TLS Options". Think of these options as different ways to make the security lock on your website even stronger and more tailored to your needs.
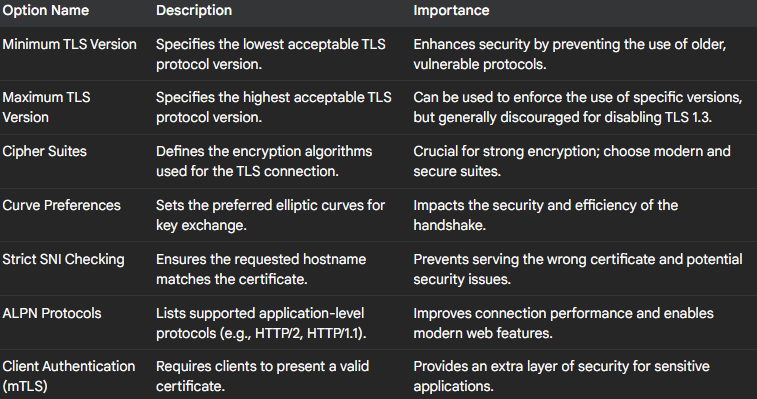
One important set of options involves setting the Minimum and Maximum TLS Version. You can tell Traefik to only allow connections that use a certain version of TLS or higher, such as TLS 1.2 or the more recent and secure TLS 1.3. This is like saying, "Only use the newest and most robust type of lock available." Older versions of TLS might have known security weaknesses, so enforcing the use of more recent versions is a critical security practice. Conversely, while you can specify a maximum version, it's generally advised against disabling TLS 1.3, as it incorporates the latest security enhancements.
Another key aspect of TLS configuration involves Cipher Suites. These are the specific algorithms used to perform the encryption, the actual "secret code" itself. Traefik allows you to choose which cipher suites it should support. It's important to select strong and modern cipher suites that are resistant to known attacks. Think of it as choosing a very complex and unbreakable code for your secret messages.
The Curve Preferences option lets you specify the order in which Traefik should prefer certain types of mathematical curves during the process of setting up the secure connection. These curves are part of the Elliptic Curve Diffie-Hellman (ECDHE) key exchange, a secure method for two parties to agree on a shared secret. Prioritizing more secure curves enhances the handshake process.
Strict SNI Checking is another valuable option. SNI, or Server Name Indication, is like when you call a large office building and tell the receptionist which company you're trying to reach. When you connect to an HTTPS server that hosts multiple websites, your browser sends the name of the website you're trying to visit as part of the initial connection. Enabling strict SNI checking ensures that Traefik will only respond if the server name provided by the client matches one of the configured certificates. This prevents the server from accidentally presenting the wrong security certificate, which could lead to security warnings in the user's browser.
ALPN Protocols, or Application-Layer Protocol Negotiation, allows you to define a list of supported protocols (like HTTP/2 or HTTP/1.1) that Traefik will offer during the TLS handshake, in order of preference. This negotiation allows the client and server to agree on the most efficient protocol to use for communication, potentially improving website performance.
For highly sensitive applications, Traefik also supports Client Authentication, often referred to as mutual TLS (mTLS). This is like having a double identification check. Not only does the website present a certificate to your computer to prove its identity, but your computer also needs to present a certificate to the website to prove its identity. This ensures that both parties in the communication are who they claim to be, adding an extra layer of security.
Here's an example of how you might configure some of these TLS options in Traefik using a YAML configuration file:
```
tls:
options:
default:
minVersion: VersionTLS12
cipherSuites:
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
sniStrict: true
```
In this example, we've defined a set of default TLS options. We've specified that the minimum acceptable TLS version should be 1.2, we've chosen a specific secure cipher suite for encryption, and we've enabled strict SNI checking. This ensures a baseline level of security for all TLS connections handled by Traefik that use these default options.
To summarize, here's a table of some common TLS options in Traefik:
<center>
</center>
# Getting Your Free Security Certificate: Traefik's certResolver and Let's Encrypt
Obtaining a TLS certificate for your website used to be a somewhat complicated and often costly process. However, thanks to initiatives like Let's Encrypt, getting a valid certificate is now free and much simpler.
Traefik has a powerful feature called certResolver that can automatically handle the entire process of obtaining and managing these TLS certificates, especially with providers like Let's Encrypt. Think of certResolver as your automated certificate manager. It can communicate directly with Let's Encrypt (or other certificate authorities) to request and renew certificates for your website without you having to do it manually.
So, how does it work? Imagine you want your website to have that "HTTPS" badge, showing it's secure. You need a TLS certificate, which is like a digital ID card for your website. Let's Encrypt is like a free online ID card office. Traefik's certResolver acts like your personal assistant who goes to this office, fills out all the necessary paperwork, and gets the ID card (certificate) for your website automatically.
To ensure that you actually own the domain name you're requesting a certificate for, Let's Encrypt uses different methods called "challenges". Here are some of the most common ones:
- HTTP Challenge: Let's Encrypt asks Traefik to place a special file with a specific content on your website at a well-known location. Let's Encrypt then tries to access this file. If they can successfully access it and the content matches what they expect, they know you have control over the domain.
- DNS Challenge: For this challenge, you need to add a specific record to your domain's DNS (Domain Name System) settings. Let's Encrypt then checks if this record exists and has the correct value to verify your ownership of the domain. This method is often preferred for obtaining wildcard certificates, which secure all subdomains of a domain (e.g., *.example.com).
- TLS Challenge: In this method, Traefik proves its control over the domain by responding to Let's Encrypt over a TLS connection established on port 443.
Here's a basic example of how you might configure a certResolver in Traefik using the HTTP challenge with Let's Encrypt in a YAML configuration file :
```
certificatesResolvers:
myhttpchallenge:
acme:
email: "your-email@example.com"
storage: "acme.json"
httpChallenge:
entryPoint: web
```
Let's break down this configuration:
- certificatesResolvers: This is the main section where you define your certificate resolvers.
- myhttpchallenge: This is the name we've given to our certificate resolver. You can choose any descriptive name you like.
- acme: This indicates that we want to use the ACME (Automatic Certificate Management Environment) protocol, which is the protocol Let's Encrypt uses.
- email: Here, you should provide your valid email address. Let's Encrypt will use this to contact you if there are any issues with your certificates, such as upcoming expiration.
- storage: This specifies the location where Traefik will store the certificates it obtains from Let's Encrypt. acme.json is a common convention for this file. It's crucial to ensure that this file persists across Traefik restarts. If Traefik loses access to this file, it might try to request new certificates every time it starts, which could quickly lead to hitting Let's Encrypt's rate limits.
- httpChallenge: This section tells Traefik that we want to use the HTTP challenge to prove ownership of our domain to Let's Encrypt.
- entryPoint: web: This specifies the entry point that Let's Encrypt should use to reach our server on port 80 (usually the standard port for HTTP) to perform the HTTP challenge.
It's worth noting that the DNS challenge is another popular option, especially when you need wildcard certificates to secure multiple subdomains. Configuring the DNS challenge often involves providing Traefik with specific credentials for your DNS provider so that Traefik can automatically add and remove the necessary DNS records during the challenge process.
# Telling Traefik Which Doors to Lock: Using the domains Option
Once you've configured a certResolver, you need to tell Traefik which specific domain names should use this resolver to obtain a TLS certificate. This is where the domains option comes into play.
Within the TLS configuration of a router, you can specify the main domain name and any additional alternative domain names (also known as Subject Alternative Names or SANs) that should be included in the certificate. For instance, if you want your website to be accessible at both example.com and www.example.com, you would configure both of these in the domains section.
Here's an example of how you might use the domains option in a Traefik router configuration using YAML:
```
http:
routers:
my-website:
rule: "Host(`example.com`) |
| Host(`www.example.com`)"
entryPoints:
- websecure
tls:
certResolver: myhttpchallenge
domains:
- main: "example.com"
sans:
- "www.example.com"
```
Let's break down this example:
- http.routers: This section defines our HTTP routers.
- my-website: This is the name we've given to this particular router.
- rule: "Host(\example.com`) | | Host(`www.example.com`)": This rule tells Traefik that this router should handle incoming HTTP requests for either theexample.comor thewww.example.com` domain.
- entryPoints: - websecure: This specifies that this router should use the websecure entry point, which is typically configured to listen on port 443 for HTTPS traffic.
- tls: This section configures the TLS settings for this router.
- certResolver: myhttpchallenge: Here, we're telling this router to use the certificate resolver named myhttpchallenge that we configured in the previous section to obtain its TLS certificate.
- domains: This is where we specify the domain names that should be included in the certificate.
- main: "example.com": This defines the primary domain name for the certificate.
- sans: - "www.example.com": This specifies a Subject Alternative Name. The generated certificate will also be valid for www.example.com. You can include multiple SANs in this list if your website is accessible through other domain names as well.
It's important to remember that for Let's Encrypt to successfully issue a certificate for the domains you specify in the domains option, each of those domain names (both the main domain and any SANs) must have a DNS record that points to the IP address of your Traefik instance. This allows Let's Encrypt to verify that you indeed control these domains during the challenge process.
While we've focused on configuring TLS at the router level, it's also possible to configure TLS settings, including the certResolver and domains, at the entry point level. This can be a convenient way to enforce HTTPS for all routers that are associated with that particular entry point, simplifying the overall configuration in some scenarios.
# Conclusion: A Safer Website for Everyone
Properly configuring TLS in Traefik is a fundamental step in securing your web applications and ensuring a safe and trustworthy experience for your users. By implementing TLS, you protect sensitive information from prying eyes, establish the authenticity of your website, and maintain the integrity of the data exchanged.
Traefik's powerful features, such as the ability to customize TLS connections through various options, the automated certificate management provided by certResolver (especially with Let's Encrypt), and the precise control over secured domains offered by the domains option, make it easier than ever to implement robust HTTPS for your websites. Taking the time to understand and configure these features will not only enhance the security of your online presence but also build trust with your visitors, ultimately contributing to a better user experience. So, go ahead, put on those strong locks, and make the internet a little bit safer for everyone.
---
*If you liked this content I’d appreciate an upvote or a comment. That helps me improve the quality of my posts as well as getting to know more about you, my dear reader.*
*Muchas gracias!*
*Follow me for more content like this.*
*[X](https://twitter.com/edca3911) | [PeakD](https://peakd.com/@simplestack) | [Rumble](https://rumble.com/user/simplestack) | [YouTube](https://www.youtube.com/@simple-stack-by-ed) | [Linked In](https://www.linkedin.com/in/edwardcasanova/) | [GitHub](https://github.com/ed3899) | [PayPal.me](https://paypal.me/edca3899?country.x=MX&locale.x=es_XC) | [Medium](https://medium.com/@ed.wacc1995/subscribe)*
*Down below you can find other ways to tip my work.*
```
BankTransfer: "710969000019398639", // CLABE
BAT: "0x33CD7770d3235F97e5A8a96D5F21766DbB08c875",
ETH: "0x33CD7770d3235F97e5A8a96D5F21766DbB08c875",
BTC: "33xxUWU5kjcPk1Kr9ucn9tQXd2DbQ1b9tE",
ADA: "addr1q9l3y73e82hhwfr49eu0fkjw34w9s406wnln7rk9m4ky5fag8akgnwf3y4r2uzqf00rw0pvsucql0pqkzag5n450facq8vwr5e",
DOT: "1rRDzfMLPi88RixTeVc2beA5h2Q3z1K1Uk3kqqyej7nWPNf",
DOGE: "DRph8GEwGccvBWCe4wEQsWsTvQvsEH4QKH",
DAI: "0x33CD7770d3235F97e5A8a96D5F21766DbB08c875"
``` hiveblocks
hiveblocks