<center></center>
<p>
In this post, I'm going to examine attacks called SQL Injection attacks.
</p>
<h3>
What is SQL Injection?
</h3>
<p>
When it comes to SQL Injection, many web programmers and website administrators are afraid and think that they're dealing with a very complicated topic! So first of all I have to tell you that there is nothing to worry about. All you have to do is get rid of some bad habits and learn some new ones. In other words, we don't need any special operation and complex design, but we should write our queries in the appropriate format and based on the correct format so that they are completely safe. simply!
</p>
<p>
Unfortunately, although preventing SQL Injection is very simple, it is still one of the most common and important reasons for website hacking in the world. Part of the blame lies with webmasters who hire programmers who want lower salaries rather than those with more expertise. Another part of the blame lies with programmers who think that by learning programming commands, they will become programmers and do not make any effort to maintain the security of a website, instead they take their rights and quickly deliver the website. Try to be ethical and do not make and sell in your job.
</p>
<p>
Technically, SQL Injection is:
</p>
<pre><code class="language-plaintext">SQL injection is a code injection technique, used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker)</code></pre>
<p>
But if I want to say in simpler language:
</p>
<pre><code class="language-plaintext">SQL Injection is an exploit of improperly formatted SQL queries. The root of this type of attack is the combination of code and data.</code></pre>
<p>
In fact, SQL queries are a program just like PHP scripts, but the difference is that we build this program dynamically and add things to it as we go (which is usually from the user's side). In such a situation, it is natural that some codes change the structure of our program or disrupt its execution. Such a situation occurs only when we have not formatted our query correctly.
</p>
<p>
The following image is one of the jokes of users and programmers regarding SQL Injection, which has been spread in cyberspace:
</p>
<center>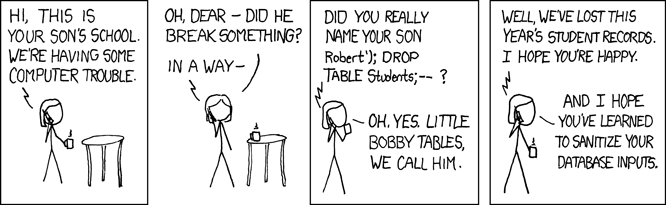</center>
<p>
If you have a little familiarity with SQL Injection, you will understand the joke of this picture, but if you don't understand anything, that's okay. I want to make an example about SQL Injection based on this joke! To understand this joke, you should know that SQL Injection attacks occur from the user's side and with the user's data. For example, you want the user to give you some amount. For example, in a form you ask the user age or name, or in the <code>login</code> form you ask for a user account and password, or even in the comments, you ask users for their opinion. Now suppose one of our queries is as follows:
</p>
<pre><code class="language-php">txtUserId = getRequestString("UserId");
txtSQL = "SELECT * FROM Users WHERE UserId = " + txtUserId;</code></pre>
<p>
The programming logic in SQL is such that the expression <code>1=1</code> is always considered true. Now suppose we ask the user to give us a value (for example, username) and instead of typing that value, the user enters the expression <code>105 OR 1=1</code> in the form. In this case, our query will look like this:
</p>
<pre><code class="language-php">SELECT * FROM Users WHERE UserId = 105 OR 1=1;</code></pre>
<p>
Do you see what happened? Based on the assumption that <code>1=1</code> is always correct, this query is also always correct and naturally it is always executed and returns all rows from the "<code>users</code>" table!!! Now, what if the users table had users' names and passwords or other important information? In this way, a beginner hacker can get all the information of your users!!
</p>
<p>
The same thing happened in the picture above and in the online form, instead of entering the student's name, the statement <code>Bobby' DROP TABLE users</code> was entered in the form. This statement will delete the <code>users table</code> and lose the information of all students! The following example is the same as the image above:
</p>
<pre><code class="language-php">$name = "Bobby';DROP TABLE users; -- ";
$query = "SELECT * FROM users WHERE name='$name'";</code></pre>
<p>
I have entered the name variable directly into the query, so this query turns into the following malicious code:
</p>
<pre><code class="language-php">SELECT * FROM users WHERE name='Bobby';DROP TABLE users; -- '</code></pre>
<p>
Although this situation is called SQL Injection among programmers, its practical reality is an unformatted string. Our query does not have the correct structure and format, and this is the reason for deleting the entire table and this SQL Injection.
</p>
<p>
Let's go to another example:
</p>
<pre><code class="language-php">$id = "1; DROP TABLE users;"
$id = mysqli_real_escape_string($link, $id);
$query = "SELECT * FROM users where id = $id";</code></pre>
<p>
In this example, we have asked the user to give us the <code>ID</code> or <code>username</code> and we have put it in the <code>id</code> variable. Then we have cleaned it using the <code>mysqli_real_escape_string</code> function and finally it has been executed. This query becomes the following safe query:
</p>
<pre><code class="language-php">SELECT * FROM users WHERE id =1;DROP TABLE users; -- '</code></pre>
<p>
Although the above code does not cause any danger, the discussion here is not only about whether it is dangerous or not. Imagine a boy named Leo O'Hara and he wants to enroll in the school system. If we do not correct our query format, we will encounter the following code:
</p>
<pre><code class="language-php">INSERT INTO users SET name='Leo O'Hara'</code></pre>
<p>
Because of the sign ' in this boy's family, we encounter a grammatical error.
</p>
<p>
</p>
<p>[Hive: @albro]</p>| author | albro | ||||||
|---|---|---|---|---|---|---|---|
| permlink | what-is-sql-injection-by-albro | ||||||
| category | hive-169321 | ||||||
| json_metadata | "{"app":"peakd/2023.11.3","format":"markdown","author":"albro","description":"In this post, I'm going to examine attacks called SQL Injection attacks.","tags":["programming","development","gosh","threads","chessbrothers","neoxian","stem","tricks","hive-engine","leofinance"],"users":["albro"],"image":["https://files.peakd.com/file/peakd-hive/albro/23qrSeQei4qN64ebjKhfmZx7qok5bYpvvkEELqQAUzcdAS6VC63beUGoVqSMNNSKzv8aN.jpg","https://files.peakd.com/file/peakd-hive/albro/23tSwyU2EhygDkMuZF53gH1wmqMqK95og5iw3BsEDQ42oCghGCnL58zEYKRcZ6N8vRjhB.png"]}" | ||||||
| created | 2023-12-22 12:44:18 | ||||||
| last_update | 2023-12-22 12:44:18 | ||||||
| depth | 0 | ||||||
| children | 2 | ||||||
| last_payout | 2023-12-29 12:44:18 | ||||||
| cashout_time | 1969-12-31 23:59:59 | ||||||
| total_payout_value | 1.440 HBD | ||||||
| curator_payout_value | 1.408 HBD | ||||||
| pending_payout_value | 0.000 HBD | ||||||
| promoted | 0.000 HBD | ||||||
| body_length | 6,389 | ||||||
| author_reputation | 30,477,419,385,789 | ||||||
| root_title | "What Is SQL Injection By albro" | ||||||
| beneficiaries |
| ||||||
| max_accepted_payout | 1,000,000.000 HBD | ||||||
| percent_hbd | 10,000 | ||||||
| post_id | 129,894,437 | ||||||
| net_rshares | 6,077,305,619,750 | ||||||
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| kevinwong | 0 | 2,141,903,259 | 0.4% | ||
| eric-boucher | 0 | 2,141,094,331 | 0.4% | ||
| thecryptodrive | 0 | 9,472,910,951 | 0.16% | ||
| roelandp | 0 | 41,820,721,795 | 5% | ||
| cloh76 | 0 | 533,137,092 | 0.4% | ||
| jeffjagoe | 0 | 2,123,447,685 | 0.5% | ||
| arcange | 0 | 211,537,314,722 | 1% | ||
| lordvader | 0 | 4,940,544,010 | 0.8% | ||
| rmach | 0 | 2,182,094,855 | 5% | ||
| lemouth | 0 | 280,539,433,710 | 10% | ||
| lamouthe | 0 | 750,998,016 | 10% | ||
| tfeldman | 0 | 742,651,739 | 0.4% | ||
| metabs | 0 | 1,058,594,504 | 10% | ||
| mcsvi | 0 | 127,128,656,854 | 50% | ||
| lk666 | 0 | 75,547,776,568 | 100% | ||
| cnfund | 0 | 1,607,762,035 | 0.8% | ||
| justyy | 0 | 4,380,639,970 | 0.8% | ||
| curie | 0 | 53,581,351,428 | 0.8% | ||
| modernzorker | 0 | 516,442,485 | 0.56% | ||
| techslut | 0 | 26,721,714,074 | 4% | ||
| steemstem | 0 | 184,190,231,491 | 10% | ||
| edb | 0 | 739,434,088 | 1% | ||
| walterjay | 0 | 67,481,821,148 | 5% | ||
| valth | 0 | 1,530,689,525 | 5% | ||
| metroair | 0 | 3,626,176,632 | 0.8% | ||
| dna-replication | 0 | 347,071,979 | 10% | ||
| privex | 0 | 468,713,948 | 0.8% | ||
| dhimmel | 0 | 53,233,221,165 | 2.5% | ||
| detlev | 0 | 2,022,854,553 | 0.24% | ||
| lizanomadsoul | 0 | 2,353,012,590 | 1% | ||
| federacion45 | 0 | 1,197,947,328 | 0.4% | ||
| gamersclassified | 0 | 531,430,314 | 0.4% | ||
| iansart | 0 | 617,547,577 | 0.4% | ||
| mobbs | 0 | 15,089,903,629 | 5% | ||
| jerrybanfield | 0 | 2,630,257,484 | 0.8% | ||
| rt395 | 0 | 2,050,267,456 | 1.5% | ||
| bitrocker2020 | 0 | 1,236,020,106 | 0.12% | ||
| sustainablyyours | 0 | 3,472,042,955 | 5% | ||
| arunava | 0 | 2,522,718,409 | 0.32% | ||
| samminator | 0 | 6,725,833,080 | 5% | ||
| enjar | 0 | 6,711,436,689 | 0.72% | ||
| lorenzor | 0 | 1,306,559,560 | 50% | ||
| derosnec | 0 | 840,029,492 | 4% | ||
| paulag | 0 | 11,969,780,009 | 10% | ||
| alexander.alexis | 0 | 6,069,676,700 | 10% | ||
| dandesign86 | 0 | 16,189,799,696 | 8% | ||
| jayna | 0 | 1,084,379,677 | 0.16% | ||
| guchtere | 0 | 492,845,980 | 4% | ||
| princessmewmew | 0 | 1,060,588,826 | 0.4% | ||
| joeyarnoldvn | 0 | 474,041,326 | 1.47% | ||
| gunthertopp | 0 | 10,814,700,816 | 0.2% | ||
| empath | 0 | 565,936,614 | 0.4% | ||
| eturnerx | 0 | 12,743,861,106 | 1.2% | ||
| minnowbooster | 0 | 1,071,686,201,871 | 20% | ||
| felt.buzz | 0 | 1,436,788,453 | 0.2% | ||
| howo | 0 | 330,120,844,227 | 10% | ||
| tsoldovieri | 0 | 1,010,553,255 | 5% | ||
| steemwizards | 0 | 610,019,305 | 0.8% | ||
| neumannsalva | 0 | 658,503,995 | 0.4% | ||
| wargof | 0 | 1,200,414,831 | 65% | ||
| stayoutoftherz | 0 | 22,968,192,352 | 0.2% | ||
| abigail-dantes | 0 | 3,644,797,992 | 10% | ||
| pixelfan | 0 | 56,859,087,657 | 6% | ||
| zonguin | 0 | 494,998,180 | 2.5% | ||
| investingpennies | 0 | 2,883,132,269 | 0.8% | ||
| khalil319 | 0 | 1,778,972,835 | 10% | ||
| iamphysical | 0 | 781,527,573 | 90% | ||
| zyx066 | 0 | 620,911,366 | 0.24% | ||
| revo | 0 | 1,623,196,054 | 0.8% | ||
| azulear | 0 | 1,186,889,328 | 100% | ||
| psicoluigi | 0 | 750,030,193 | 50% | ||
| rocky1 | 0 | 113,590,045,367 | 0.12% | ||
| thelordsharvest | 0 | 643,125,535 | 0.8% | ||
| sumant | 0 | 644,880,434 | 0.4% | ||
| aidefr | 0 | 1,031,548,273 | 5% | ||
| cloudspyder | 0 | 9,272,635,928 | 100% | ||
| sorin.cristescu | 0 | 25,768,740,380 | 5% | ||
| fatman | 0 | 9,211,986,834 | 2% | ||
| votehero | 0 | 13,443,795,817 | 2.8% | ||
| inthenow | 0 | 20,569,017,906 | 20% | ||
| yangyanje | 0 | 1,104,455,281 | 0.4% | ||
| splash-of-angs63 | 0 | 6,314,996,682 | 60% | ||
| jlsplatts | 0 | 22,682,564,263 | 2% | ||
| deadzy | 0 | 501,338,695 | 10% | ||
| meno | 0 | 3,389,494,818 | 0.4% | ||
| isnochys | 0 | 9,256,176,404 | 5% | ||
| technicalside | 0 | 28,722,605,509 | 25% | ||
| doifeellucky | 0 | 524,637,978 | 0.4% | ||
| enzor | 0 | 598,940,189 | 10% | ||
| bartosz546 | 0 | 828,218,133 | 0.4% | ||
| dreamm | 0 | 3,134,590,553 | 50% | ||
| dandays | 0 | 4,770,645,087 | 0.32% | ||
| socent | 0 | 984,897,530 | 15% | ||
| postpromoter | 0 | 233,075,219,005 | 10% | ||
| bluefinstudios | 0 | 486,990,782 | 0.24% | ||
| steveconnor | 0 | 674,693,208 | 0.4% | ||
| aboutcoolscience | 0 | 13,836,243,775 | 10% | ||
| sandracarrascal | 0 | 491,790,448 | 50% | ||
| helpie | 0 | 9,626,174,914 | 8% | ||
| kenadis | 0 | 2,683,329,135 | 10% | ||
| madridbg | 0 | 4,913,972,211 | 10% | ||
| robotics101 | 0 | 3,002,309,938 | 10% | ||
| elex17 | 0 | 1,319,305,797 | 100% | ||
| punchline | 0 | 1,134,621,195 | 0.8% | ||
| markaustin | 0 | 794,766,435 | 5% | ||
| soulturtle | 0 | 474,463,616 | 1.6% | ||
| duke77 | 0 | 1,084,438,248 | 40% | ||
| r00sj3 | 0 | 17,233,298,165 | 5% | ||
| sco | 0 | 2,918,120,451 | 10% | ||
| ennyta | 0 | 956,718,750 | 50% | ||
| juecoree | 0 | 740,144,286 | 7% | ||
| vjap55 | 0 | 7,922,940,773 | 100% | ||
| nerdtopiade | 0 | 546,873,176 | 2.75% | ||
| dudeontheweb | 0 | 1,759,550,476 | 1.75% | ||
| carn | 0 | 486,915,855 | 0.72% | ||
| hetty-rowan | 0 | 574,491,947 | 0.4% | ||
| ydavgonzalez | 0 | 2,012,737,805 | 10% | ||
| intrepidphotos | 0 | 2,265,047,496 | 7.5% | ||
| fineartnow | 0 | 546,075,287 | 0.4% | ||
| slacktmusic | 0 | 723,303,238 | 4% | ||
| communitybank | 0 | 527,492,511 | 0.8% | ||
| fragmentarion | 0 | 5,738,397,133 | 10% | ||
| bennettitalia | 0 | 2,846,023,940 | 4% | ||
| utube | 0 | 582,720,684 | 0.8% | ||
| manncpt | 0 | 1,645,676,192 | 1% | ||
| dynamicrypto | 0 | 1,294,861,942 | 1% | ||
| neneandy | 0 | 883,577,272 | 0.8% | ||
| marc-allaria | 0 | 611,294,207 | 0.4% | ||
| goldrooster | 0 | 1,369,639,360 | 100% | ||
| sportscontest | 0 | 767,461,695 | 0.8% | ||
| gribouille | 0 | 935,911,876 | 20% | ||
| itharagaian | 0 | 2,747,880,048 | 40% | ||
| pandasquad | 0 | 2,075,386,887 | 0.8% | ||
| jakeeyexe | 0 | 653,710,281 | 50% | ||
| tobias-g | 0 | 17,516,177,940 | 5% | ||
| cool08 | 0 | 439,866,707 | 5% | ||
| miguelangel2801 | 0 | 766,619,238 | 50% | ||
| fantasycrypto | 0 | 561,703,688 | 0.8% | ||
| warpedpoetic | 0 | 3,016,538,528 | 8% | ||
| emiliomoron | 0 | 1,466,031,048 | 5% | ||
| photohunt | 0 | 541,086,856 | 0.8% | ||
| geopolis | 0 | 622,736,036 | 10% | ||
| robertbira | 0 | 1,040,493,863 | 2.5% | ||
| alexdory | 0 | 1,467,354,992 | 10% | ||
| takowi | 0 | 12,863,691,488 | 0.8% | ||
| irgendwo | 0 | 3,194,955,555 | 0.8% | ||
| samostically | 0 | 782,483,772 | 50% | ||
| cyprianj | 0 | 5,421,537,592 | 5% | ||
| melvin7 | 0 | 15,927,995,431 | 5% | ||
| francostem | 0 | 1,343,313,659 | 10% | ||
| endopediatria | 0 | 686,733,630 | 20% | ||
| croctopus | 0 | 1,450,530,617 | 100% | ||
| jjerryhan | 0 | 756,903,414 | 0.4% | ||
| zipporah | 0 | 3,955,851,759 | 1.6% | ||
| superlotto | 0 | 2,094,753,306 | 0.8% | ||
| oadissin | 0 | 13,724,441,474 | 5% | ||
| doomsdaychassis | 0 | 1,431,071,485 | 8% | ||
| bscrypto | 0 | 2,071,094,100 | 0.4% | ||
| movingman | 0 | 520,544,331 | 20% | ||
| jeronimorubio | 0 | 816,291,513 | 8% | ||
| tomastonyperez | 0 | 16,505,622,590 | 50% | ||
| elvigia | 0 | 10,813,542,882 | 50% | ||
| sanderjansenart | 0 | 753,928,069 | 0.4% | ||
| qberry | 0 | 534,776,836 | 0.4% | ||
| kanrat | 0 | 1,049,108,802 | 1.62% | ||
| greddyforce | 0 | 559,875,180 | 0.29% | ||
| braaiboy | 0 | 1,459,705,517 | 0.4% | ||
| gadrian | 0 | 63,901,527,269 | 7.5% | ||
| therising | 0 | 14,113,847,106 | 0.8% | ||
| eniolw | 0 | 17,627,280,794 | 100% | ||
| de-stem | 0 | 5,452,295,480 | 9.9% | ||
| imcore | 0 | 864,029,264 | 10% | ||
| misterlangdon | 0 | 1,366,547,714 | 50% | ||
| josedelacruz | 0 | 4,723,693,711 | 50% | ||
| achimmertens | 0 | 2,294,084,743 | 0.4% | ||
| kgakakillerg | 0 | 18,533,265,361 | 10% | ||
| we-are-one | 0 | 0 | 3.8% | ||
| erickyoussif | 0 | 654,170,519 | 100% | ||
| deholt | 0 | 539,863,316 | 8.5% | ||
| robmolecule | 0 | 22,338,175,559 | 10% | ||
| pladozero | 0 | 29,396,689,586 | 10% | ||
| minerthreat | 0 | 480,539,058 | 0.4% | ||
| nateaguila | 0 | 82,506,568,405 | 5% | ||
| davidesimoncini | 0 | 469,208,574 | 100% | ||
| crypticat | 0 | 1,383,928,308 | 0.4% | ||
| temitayo-pelumi | 0 | 879,158,782 | 10% | ||
| millibot | 0 | 3,343,782,189 | 48.54% | ||
| free-reign | 0 | 1,418,020,999 | 1.2% | ||
| andrick | 0 | 833,663,070 | 50% | ||
| doctor-cog-diss | 0 | 8,995,932,513 | 10% | ||
| dailyspam | 0 | 12,958,691,207 | 20% | ||
| uche-nna | 0 | 948,694,233 | 0.64% | ||
| citizendog | 0 | 671,869,227 | 0.8% | ||
| letenebreux | 0 | 1,626,395,444 | 40% | ||
| cheese4ead | 0 | 630,795,443 | 0.4% | ||
| mafufuma | 0 | 6,946,071,179 | 1% | ||
| apshamilton | 0 | 1,969,396,907 | 0.1% | ||
| gaottantacinque | 0 | 424,364,302 | 100% | ||
| nattybongo | 0 | 18,204,033,271 | 10% | ||
| roozeec | 0 | 499,256,964 | 10% | ||
| bflanagin | 0 | 608,593,211 | 0.4% | ||
| melor9 | 0 | 666,874,702 | 4% | ||
| lillywilton | 0 | 2,066,853,348 | 20% | ||
| hamismsf | 0 | 620,411,305 | 0.1% | ||
| goblinknackers | 0 | 74,017,224,524 | 7% | ||
| anttn | 0 | 4,597,278,271 | 0.4% | ||
| kylealex | 0 | 4,689,367,863 | 10% | ||
| gasaeightyfive | 0 | 758,222,676 | 100% | ||
| orlandogonzalez | 0 | 3,287,655,010 | 25% | ||
| voxmortis | 0 | 553,288,900 | 0.32% | ||
| fran.frey | 0 | 4,062,232,276 | 50% | ||
| jrevilla | 0 | 654,935,842 | 100% | ||
| thelittlebank | 0 | 2,920,305,732 | 0.4% | ||
| pboulet | 0 | 20,175,708,644 | 8% | ||
| cercle | 0 | 2,086,662,100 | 40% | ||
| marcocasario | 0 | 0 | 0.01% | ||
| stem-espanol | 0 | 8,118,315,853 | 100% | ||
| voter003 | 0 | 13,369,810,054 | 5.1% | ||
| vimm | 0 | 58,029,730,599 | 5% | ||
| cribbio | 0 | 1,705,947,040 | 100% | ||
| cliffagreen | 0 | 4,912,834,224 | 10% | ||
| aleestra | 0 | 12,432,031,800 | 80% | ||
| l-singclear | 0 | 1,858,830,097 | 100% | ||
| brianoflondon | 0 | 11,690,227,799 | 0.2% | ||
| priyanarc | 0 | 61,327,132,217 | 60% | ||
| giulyfarci52 | 0 | 1,659,629,238 | 50% | ||
| esthersanchez | 0 | 4,216,093,734 | 60% | ||
| kristall97 | 0 | 2,969,298,094 | 100% | ||
| steemcryptosicko | 0 | 1,247,003,184 | 0.16% | ||
| stem.witness | 0 | 556,937,859 | 10% | ||
| chipdip | 0 | 790,402,617 | 10% | ||
| jpbliberty | 0 | 1,147,977,462 | 0.2% | ||
| shainemata | 0 | 2,689,871,009 | 1% | ||
| vaultec | 0 | 6,496,890,183 | 12% | ||
| steemstorage | 0 | 954,809,678 | 0.8% | ||
| crowdwitness | 0 | 26,673,112,547 | 5% | ||
| helpie-caster | 0 | 1,399,752,770 | 3.25% | ||
| steemean | 0 | 10,095,718,091 | 5% | ||
| aaronkroeblinger | 0 | 116,104,356,015 | 50% | ||
| cryptofiloz | 0 | 1,245,131,471 | 0.8% | ||
| larsito | 0 | 5,134,815,959 | 60% | ||
| robibasa | 0 | 17,890,100,245 | 10% | ||
| tinyhousecryptos | 0 | 475,603,553 | 5% | ||
| rtron86 | 0 | 6,229,916,243 | 50% | ||
| reggaesteem | 0 | 497,939,620 | 5% | ||
| bedazzled | 0 | 92,072,288,098 | 100% | ||
| beta500 | 0 | 506,051,248 | 0.8% | ||
| bastionpm | 0 | 949,413,774 | 40% | ||
| elianaicgomes | 0 | 762,979,300 | 5% | ||
| steemstem-trig | 0 | 165,188,865 | 10% | ||
| baltai | 0 | 877,017,138 | 0.4% | ||
| atheistrepublic | 0 | 949,500,522 | 0.4% | ||
| ibt-survival | 0 | 34,419,776,356 | 10% | ||
| curacer | 0 | 3,462,844,202 | 50% | ||
| lightpaintershub | 0 | 618,046,207 | 1% | ||
| keys-defender | 0 | 3,555,783,121 | 100% | ||
| hivebuzz | 0 | 4,521,426,755 | 1% | ||
| laruche | 0 | 1,317,517,477 | 0.65% | ||
| stemsocial | 0 | 83,575,398,514 | 10% | ||
| holoferncro | 0 | 4,605,569,648 | 10% | ||
| ciderjunkie | 0 | 1,517,595,254 | 2.43% | ||
| louis00334 | 0 | 2,196,447,070 | 50% | ||
| hive-143869 | 0 | 285,769,262,390 | 40% | ||
| emrysjobber | 0 | 762,334,805 | 25% | ||
| noelyss | 0 | 3,434,537,596 | 5% | ||
| balvinder294 | 0 | 4,785,276,756 | 20% | ||
| lithajacobs | 0 | 2,794,800,260 | 100% | ||
| quinnertronics | 0 | 15,672,056,822 | 7% | ||
| buildahouse | 0 | 1,114,029,045 | 40% | ||
| portsundries | 0 | 2,780,719,753 | 100% | ||
| hive-108278 | 0 | 511,808,155 | 30% | ||
| gohive | 0 | 3,092,899,830 | 100% | ||
| doudoer | 0 | 710,804,059 | 50% | ||
| emeraldtiger | 0 | 2,812,035,022 | 20% | ||
| meritocracy | 0 | 8,928,700,787 | 0.08% | ||
| jmsansan | 0 | 618,872,154 | 0.4% | ||
| eumorrell | 0 | 2,458,995,745 | 100% | ||
| he-index | 0 | 8,901,462,035 | 10% | ||
| dcrops | 0 | 5,072,261,392 | 0.4% | ||
| entraide.rewards | 0 | 1,288,740,190 | 40% | ||
| peerfinance | 0 | 53,031,207,000 | 100% | ||
| cookaiss | 0 | 6,880,325,047 | 20% | ||
| arunbiju969 | 0 | 553,195,548 | 14% | ||
| moraviareosa | 0 | 3,765,594 | 100% | ||
| nfttunz | 0 | 1,282,494,956 | 0.08% | ||
| hive-defender | 0 | 564,418,679 | 100% | ||
| key-defender.shh | 0 | 100,100,158 | 100% | ||
| holovision.cash | 0 | 3,335,806,007 | 100% | ||
| holovision.stem | 0 | 1,082,614,262 | 100% | ||
| sarashew | 0 | 537,531,271 | 0.8% | ||
| buffalobison | 0 | 27,276,154,830 | 50% | ||
| podping | 0 | 1,139,316,058 | 0.2% | ||
| mayberlys | 0 | 2,289,093,458 | 50% | ||
| irivers | 0 | 0 | 100% | ||
| pishio | 0 | 447,922,117,665 | 10% | ||
| chessbrotherspro | 0 | 348,993,457,912 | 100% | ||
| aries90 | 0 | 6,578,799,862 | 0.8% | ||
| alloyxuast | 0 | 12,548,144,673 | 50% | ||
| gambit-x | 0 | 4,817,945,145 | 100% | ||
| poolpartylegolas | 0 | 4,122,459,183 | 100% | ||
| michupa | 0 | 1,374,252,783 | 0.5% | ||
| iskafan | 0 | 3,890,033,588 | 30% | ||
| rosmarly | 0 | 1,681,391,818 | 100% | ||
| kingz1339 | 0 | 750,874,663 | 100% | ||
| kqaosphreak | 0 | 655,774,774 | 10% | ||
| waivio.curator | 0 | 1,766,470,150 | 3.32% | ||
| crypto-shots | 0 | 0 | 50% | ||
| oabreuf24 | 0 | 8,438,998,632 | 100% | ||
| netvalar | 0 | 6,182,260,373 | 50% | ||
| sam9999 | 0 | 678,047,913 | 5% | ||
| cryptoshots.nft | 0 | 990,941,454 | 100% | ||
| prosocialise | 0 | 8,409,259,832 | 5% | ||
| misticogama | 0 | 885,329,951 | 5% | ||
| archangel21 | 0 | 489,345,795 | 0.8% | ||
| independance | 0 | 1,327,858,312 | 40% | ||
| mugueto2022 | 0 | 552,396,327 | 20% | ||
| nazom | 0 | 1,181,901,459 | 50% | ||
| isiksenpalvoja | 0 | 651,175,788 | 40% | ||
| raca75 | 0 | 685,470,715 | 50% | ||
| sbtofficial | 0 | 672,495,195 | 0.4% | ||
| dutchchemist | 0 | 476,619,882 | 100% | ||
| cryptoshots.play | 0 | 0 | 10% | ||
| frankrey11 | 0 | 492,354,889 | 100% | ||
| ctptips | 0 | 16,526,405 | 15% | ||
| gejami | 0 | 7,187,177,998 | 100% | ||
| bgmoha | 0 | 6,729,449,209 | 100% | ||
| minava.museum | 0 | 2,579,079,231 | 40% | ||
| lordnight72 | 0 | 566,531,053 | 40% | ||
| cryptoshotsdoom | 0 | 0 | 10% | ||
| leogomez1414 | 0 | 2,263,003,454 | 25% | ||
| osran | 0 | 4,794,249,544 | 100% | ||
| hive-fr | 0 | 3,009,114,088 | 40% | ||
| humbe | 0 | 1,499,816,679 | 1% | ||
| elcholitosanto | 0 | 13,938,465,311 | 50% | ||
| peniel2010 | 0 | 1,447,138,445 | 50% | ||
| hive-179513 | 0 | 1,982,370,223 | 50% | ||
| sapphireleopard | 0 | 719,465,742 | 40% | ||
| aaronm04 | 0 | 983,290,745 | 50% | ||
| opticus | 0 | 556,946,404 | 0.4% | ||
| pars.team | 0 | 1,261,023,256 | 100% | ||
| karina.gpt | 0 | 0 | 100% | ||
| albro | 0 | 7,513,521,688 | 100% | ||
| rhemagames | 0 | 696,821,163 | 0.4% | ||
| cyclopshive | 0 | 20,939,236,076 | 50% | ||
| hive-fr-ithara | 0 | 469,059,494 | 40% | ||
| hive-fr-engine | 0 | 368,905,320 | 40% | ||
| nabab | 0 | 808,973,626 | 40% | ||
| riyaverma123 | 0 | 2,558,664,979 | 100% | ||
| ledonjon | 0 | 1,199,906,358 | 40% | ||
| snippets | 0 | 99,266,198,579 | 100% | ||
| ginabell | 0 | 0 | 100% | ||
| hive-180478 | 0 | 0 | 100% | ||
| agileautomation | 0 | 108,014,877 | 100% |
<h3>Congratulations!</h3><hr /><div class="pull-right"><img src="https://files.peakd.com/file/peakd-hive/chessbrotherspro/AJoJKGVARKHFCTHG7ee3GNkn5RMN7wixeJ52ipAgzDZ4QmeTcBdsk8hpi4pgj4e.png" alt="You have obtained a vote from CHESS BROTHERS PROJECT"/></div><div class="text-justify"><h3>✅ Good job. Your post has been appreciated and has received support from <a href="/@chessbrotherspro"><b>CHESS BROTHERS</b></a> ♔ 💪</h3><p><br>♟ We invite you to use our hashtag <b>#chessbrothers</b> and learn more <a href="/@chessbrotherspro/introducing-chess-brothers-project-the-most-innovative-community-combining-chess-fitness-and-more"><b>about us</b></a>.</p><p>♟♟ You can also reach us on our <a href="https://discord.gg/73sK9ZTGqJ" rel="noopener" title="This is going to take you to the Discord of Chess Brothers"><b>Discord server</b></a> and promote your posts there. </p><p>♟♟♟ Consider <a href="/@chessbrotherspro/teamwork-is-worthwhile-join-the-chess-brothers-healing-trail-supporting-the-work-being-done-and-earning-rewards"><b>joining our curation trail</b></a> so we work as a team and you get rewards automatically.</p><p>♞♟ Check out our <a href="/@chessbrotherspro"><b>@chessbrotherspro</b></a> account to learn about the curation process carried out daily by our team.</p><br>🥇 If you want to earn profits with your HP delegation and support our project, we invite you to join the <i>Master Investor</i> plan. <a href="/@chessbrotherspro/master-investor-plan-or-programa">Here you can learn how to do it.</a></div><div class="text-center"><p><br>Kindly</p><p><strong><em>The CHESS BROTHERS team</em></strong></p></div>
| author | chessbrotherspro |
|---|---|
| permlink | re-what-is-sql-injection-by-albro-20231223t065058z |
| category | hive-169321 |
| json_metadata | "{"app": "beem/0.24.26"}" |
| created | 2023-12-23 06:51:00 |
| last_update | 2023-12-23 06:51:00 |
| depth | 1 |
| children | 0 |
| last_payout | 2023-12-30 06:51:00 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 1,628 |
| author_reputation | 78,121,414,722,998 |
| root_title | "What Is SQL Injection By albro" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 129,919,853 |
| net_rshares | 7,812,162,469 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| albro | 0 | 7,812,162,469 | 100% |
<div class='text-justify'> <div class='pull-left'> <img src='https://stem.openhive.network/images/stemsocialsupport7.png'> </div> Thanks for your contribution to the <a href='/trending/hive-196387'>STEMsocial community</a>. Feel free to join us on <a href='https://discord.gg/9c7pKVD'>discord</a> to get to know the rest of us! Please consider delegating to the @stemsocial account (85% of the curation rewards are returned). You may also include @stemsocial as a beneficiary of the rewards of this post to get a stronger support. <br /> <br /> </div>
| author | stemsocial |
|---|---|
| permlink | re-albro-what-is-sql-injection-by-albro-20231223t065442824z |
| category | hive-169321 |
| json_metadata | {"app":"STEMsocial"} |
| created | 2023-12-23 06:54:42 |
| last_update | 2023-12-23 06:54:42 |
| depth | 1 |
| children | 0 |
| last_payout | 2023-12-30 06:54:42 |
| cashout_time | 1969-12-31 23:59:59 |
| total_payout_value | 0.000 HBD |
| curator_payout_value | 0.000 HBD |
| pending_payout_value | 0.000 HBD |
| promoted | 0.000 HBD |
| body_length | 565 |
| author_reputation | 22,919,337,499,097 |
| root_title | "What Is SQL Injection By albro" |
| beneficiaries | [] |
| max_accepted_payout | 1,000,000.000 HBD |
| percent_hbd | 10,000 |
| post_id | 129,919,897 |
| net_rshares | 7,656,681,806 |
| author_curate_reward | "" |
| voter | weight | wgt% | rshares | pct | time |
|---|---|---|---|---|---|
| albro | 0 | 7,656,681,806 | 100% |
 hiveblocks
hiveblocks